Verifiability Of Site Identity
The system involves a pop-up window or inline frame appearing during the online transaction process, requiring the cardholder to enter a password which, if the transaction is legitimate, their card issuer will be able to authenticate. The problem for the cardholder is determining if the pop-up window or frame is really from their card issuer when it could be from a fraudulent website attempting to harvest the cardholders details. Such pop-up windows or script-based frames lack any access to any security certificate, eliminating any way to confirm the credentials of the implementation of 3-DS.
The Verified-by-Visa system has drawn some criticism, since it is hard for users to differentiate between the legitimate Verified-by-Visa pop-up window or inline frame, and a fraudulent phishing site. This is because the pop-up window is served from a domain which is:
- Not the site where the user is shopping
- Not the card issuer
- Not visa.com or mastercard.com
Implementation of 3-D Secure sign-up will often not allow a user to proceed with a purchase until they have agreed to sign up to 3-D Secure and its terms and conditions, not offering any alternative way of navigating away from the page than closing it, thus suspending the transaction.
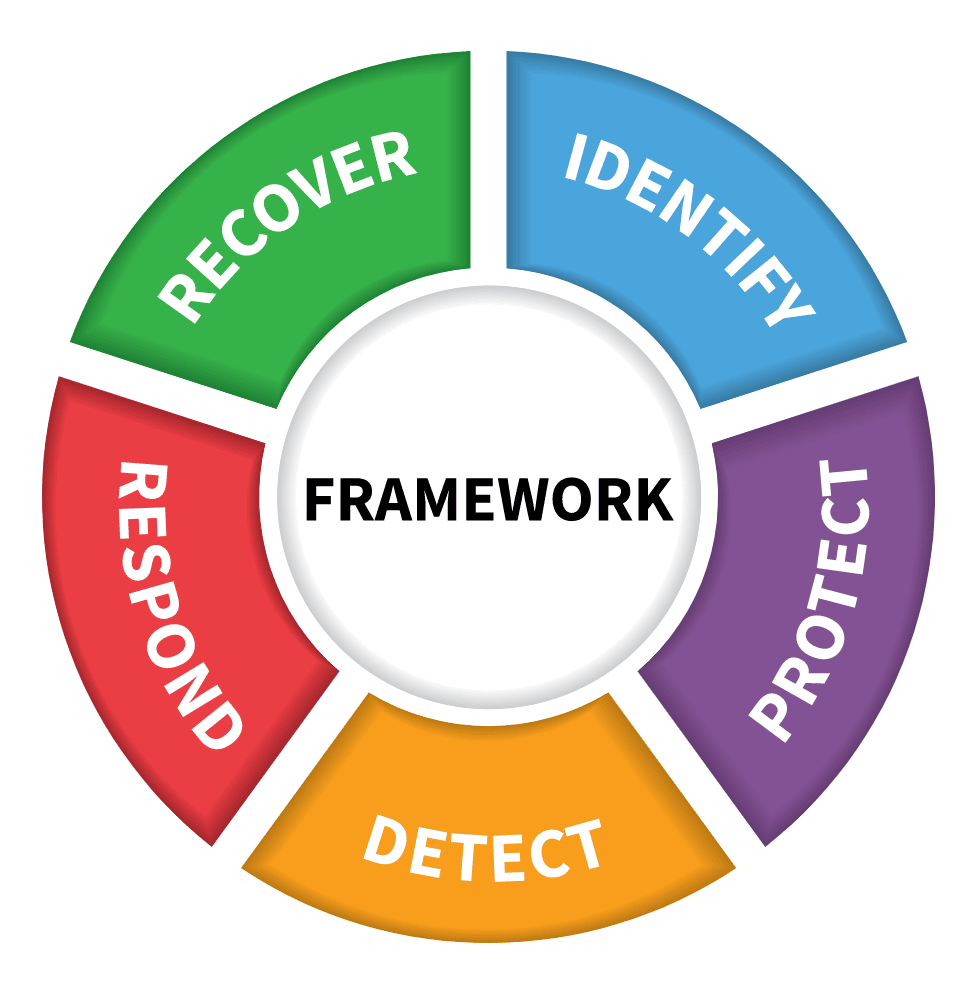
Domains Of The Nist Security Framework
The five domains in the NIST framework are the pillars support the creation of a holistic and successful cybersecurity plan. They include identify, protect, detect, respond, and recover. These five NIST functions all work concurrently and continuously to form the foundation where other essential elements can be built for successful high-profile cybersecurity risk management.
Dont Miss: How To Set Up Gmail With Your Own Domain
Domain : Security Engineering
Security engineering usually refers to two key subdomains: network security and computer operations security. This domain is where your technical expertise is put to use in securing both the network and hosts from attacks. Its in this domain that we lump the following:
- Intrusion detection and prevention systems
- Host-based security tools
Also Check: How To Make A Domain Registrar
Cloudflare Wins Cisa Contract For Registry And Authoritative Domain Name System Services
With the $7.2M contract, Cloudflare will enhance resilience and simplify security for .gov domain users
SAN FRANCISCO, January 13, 2023—-Cloudflare, Inc. , the security, performance, and reliability company helping to build a better Internet, has been awarded a $7.2 million contract from the Cybersecurity and Infrastructure Security Agency to provide Registry and Authoritative DNS services to the .gov TLD .
“The Internet has made the United States government more accessible for constituents than ever before, whether they’re applying for a passport, learning health and safety recommendations for their communities, or reaching out to a representative,” said Matthew Prince, co-founder & CEO of Cloudflare. “Having a reliable and secure DNS for government agencies is critical to instill trust in all .gov activity, and working with us to achieve this is a testament to the reliability and security of the Cloudflare network.”
CISA is the nations risk advisor, working with partners to defend against todays threats and collaborating to build more secure and resilient infrastructure for the future. CISA builds the nations capacity to defend against cyber attacks by providing cybersecurity tools, incident response capabilities, and assessment services to safeguard the Federal IT enterprise, state and local partners, and systems that support national critical functions.
For more information, visit:
Contacts
Domain : Security Management
The first domain Id like to discuss has more to do with people and processes than it does with computers. Security management is one of the most overlooked domains, which I think is a shame because almost nothing we do in the other domains means anything without it. Security management is made up of several tasks:
- Risk assessments, which is the process we use to identify risks to the organization and systemically identify methods to combat those risks, usually relying on input from experts in the below domains
- Overseeing the processes for other security functions to ensure those align with business/operations processes
- Change management processes and procedures in place
- User security awareness training
Recommended Reading: Which Domain Ending Is Best
What Is Security Domain Under Cnssi 4009what Is Security Domain Under Cnssi 4009
NIST SP 800-53 Rev. 4 under Security Domain from CNSSI 4009. An environment or context that includes a set of system resources and a set of system entities that have the right to access the resources as defined by a common security policy, security model, or security architecture. See Security Domain.
Definition Of Information Security Management System
An ISMS is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes and IT systems by applying a riskmanagementprocess. It can help small, medium and large businesses in any sector keep information assets secure.
The Information Security Management System represents the collation of all the interrelated/interacting information security elements of an organization so as to ensure policies, procedures, and objectives can be created, implemented, communicated, and evaluated to better guarantee an organizations overall information security. This system is typically influenced by organizations needs, objectives, security requirements, size, and processes. An ISMS includes and lends to effective risk management and mitigation strategies. Additionally, an organizations adoption of an ISMS largely indicates that it is systematically identifying, assessing, and managing information security risks and will be capable of successfully addressing information confidentiality, integrity, and availability requirements. However, the human factors associated with ISMS development, implementation, and practice must also be considered to best ensure the ISMS ultimate success.
Also Check: What Is A Reasonable Price For A Domain Name
The Future Is Zero Trust
Even as the world continues to change, the need for cybersecurity will remain a constant for businesses trying to protect their customers, employees, data, and IP. Cybercriminals thrive on chaos, agilely taking advantage during major disruptions to attack businesses that are defenseless. Worse, they also target enterprises that have a false sense of cybersecurity, believing their perimeters are protected and impenetrable. The most secure way forward for all business entities is to understand the limitations of traditional perimeter-based security and to step into the future by implementing the zero trust security model.
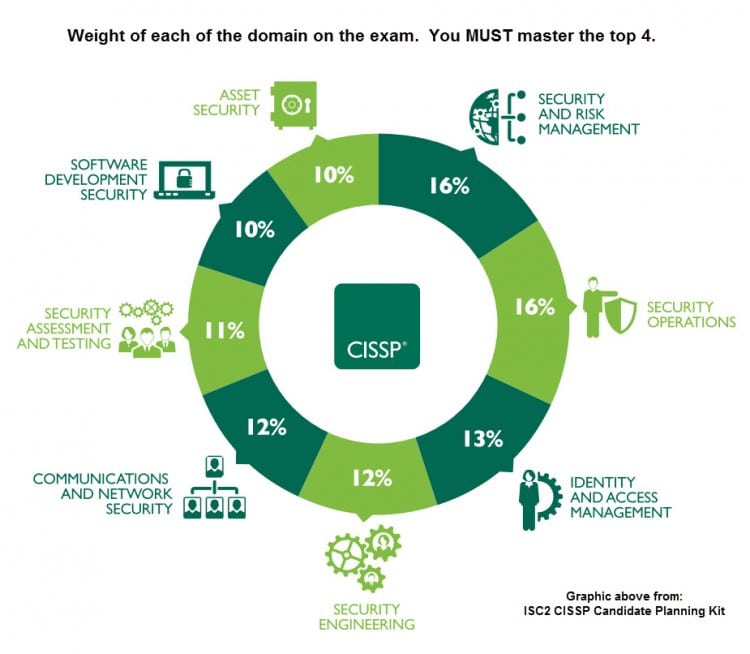
The 8 Cissp Domains Explained
The CISSP® qualification is one of the most respected certifications in the information security industry, demonstrating an advanced knowledge of cyber security.
We recently discussed the benefits of becoming a CISSP. Now, we turn our attention to the structure of the qualification itself and the domains within it.
2, which developed and maintains the CISSP qualification, updated the structure of the certificate in 2015, moving from ten domains to eight.
Well begin by listing the eight domains, and then go on to explain each one in more detail.
Read Also: How To Make Money With Domains
Three Key Elements For Building An Effective Human
. Architecture Secure Coding and Testing. Malicious Links Webmail Policies Strong Passwords. In this article we take a look at the 14 security domains specific to ISO 27001.
Each of these domains represents a distinct set of practices that need to. Empower Your Organizations Defenders by Putting the Right Tools in the Right Hands. The CISM credential focuses on four domains.
Security and risk management is one of the largest domains in cybersecurity. The security architecture domain refer to a plan and set of principles that describe the security services that a system is required to provide to meet the needs of its users the. Ad Compare Best Computer Security Software 2022.
As the name implies this security domain covers the legal issues associated with computer. Confidential Secret and Top Secret are three security domains used by the US. Information security governance information security risk management and compliance information security program development and.
A security domain is considered. A network with a different security domain is kept separate from other networks. Which of these things is part of the cyber domain.
Confidential Secret and Top Secret are three security domains used by the US. Protect Your PC From Viruses Online Threats. Department of Defense DoD for example.
Physical People and Cyber. Confidential Secret and Top Secret are three security domains used by the US. Stay Safe Online Today.
2 To build a culture of security.
Resource Sharing Across Domainsedit
Some types of resources in Elasticsearch are owned by a single user, such asasync search contexts, API keys,and user profiles. When a user creates a resource, Elasticsearchcaptures the users username and realm information as part of the resourcesmetadata. Likewise, if a user updates a resource, such as an API key,Elasticsearch automatically re-captures the users current realm information.
When a user later attempts to access the resource, Elasticsearch comparesthe captured username and realm information against those from the accessinguser. Elasticsearch will deny access unless both the realm and username match.If Elasticsearch detects that a username from two different realms isattempting to access a resource, Elasticsearch assumes that these users are distinct anddoesnt allow resources to be shared between those users.
However, there are cases where the same user can authenticate withmultiple realms and needs to share the same set of resources across realms.For example, an LDAP realm and a SAML realm canbe backed by the same directory service. Additionally, allows onerealm to delegate authorization to another realm. If both realms authenticateusers with the same username, its reasonable to treat these users as thesame user from a resource ownership perspective.
Managing roles across realmsedit
Read Also: Can You Make Your Own Domain Extension
What Are The 5 Cybersecurity Domains
A NIST Security Framework is divided into five domains. In the NIST framework, there are five domains that are critical to creating a security plan that is holistic and successful. In addition to identifying, protecting, detecting, responding, and recovering, there is also restoring.
- Is Sharksurf Vpn As Fast?
- Is Sharing A Vpn With My Neighbor?
- Is Securelink A Vpn?
Dont Miss: Transferring Domain From Wix To Shopify
Identity And Access Management
Identity and Access Management comprises about 13% of the CISSP exam.
This domain helps information security professionals understand how to control the way users can access data. It covers:
- Physical and logical access to assets
- Identification and authentication
- Integrating identity as a service and third-party identity services
- The identity and access provisioning lifecycle.
Also Check: Where Is The Cheapest Place To Buy A Domain Name
Add A Security Contact
A security contact is like building a digital front door for the public to report observed or suspected security issues at your domain. This could include notifications about compromised accounts, unsolicited email, routing problems, or reporting a potential vulnerability.
You can add a security contact at the .gov registrar, which will make it available in the .gov WHOIS and our published data. You can change your security contact at any time removing the contact withdraws it from WHOIS and our published data.
A security contact should be capable of evaluating or triaging security reports for your entire domain. We recommend using a team email address specifically for reports, and avoiding the use of an individuals email address. A common address form is security@< domain> or abuse@< domain> .
Wed also recommend placing your security contact info on your website and in organizational communications. If people cant find where to report something, having a security contact isnt helpful!
The Human Firewall Is A Crucial Element Of A Long
- Jessica Groopman,Kaleido Insights
Businesses must prioritize cybersecurity now more than ever. This process requires a broader scope than investing heavily in security technologies, however the tactic most companies have relied on to date. Relegating cybersecurity measures to IT-only mitigation overlooks the top cybersecurity risk: people.
Organizations have long deployed firewalls configurations of hardware and software that monitor and control network traffic based on predetermined security rules around their technical assets. Recently, cutting-edge AI-powered security applications came along as enhancements to the firewall concept. But, as sophisticated threats grow ever wider across distributed endpoints, targeting humans and their vulnerabilities, another kind of firewall is required: a human firewall.
Recommended Reading: How To Create Email With Own Domain In Gmail
Read Also: Can I Use My Domain Name With Wix
Introduction To Security Domains
There are many potential methods through which tofacilitate the discussion of security. Many desire to discuss security onan Enterprise basis. However, there is an issue regarding the definitionand boundaries of the Enterprise and those boundaries are always changing.Thus developing Enterprise level security constructs/policies becomesdifficult and un-productive, as they are difficult to manage.
Another method is to perform concrete analysis ofparticular systems and communication technologies/topologies. It is oftendifficult to discuss a security models in concrete terms since the technologyused in deployments typically becomes the lowest common denominator that isdiscussed. Such technology based security models tend to be difficult toscale and understand from a enterprise system perspective. Likewise, suchconcrete models are difficult to extend/scale to address systemic security.
There is another, although less used, concept. Thatis the concept discussing security in regards to atomic security domains thatrepresent security boundaries.
The concept of a security domain that is introduced inthis paper is not new. Many computer security practitioners have been using the ideas presented here for many years inprotecting networks. For instance, NERC 1200 and 1300 security requirements use the term “Electronic Perimeters” for Security Domains.
Security Assessment And Testing
Security assessment and testing determines the performance and design of an organizations security. It can be considered an extension of the risk assessment responsibility under the Security and Risk Management domain. However, security assessment and testing focuses on determining and analyzing the security processes. It observes:
- Internal and third-party security audits
- Security control testing
- Designing and validating assessment and test strategies
Don’t Miss: How To Create Custom Domain Email
The Three Domains Of Application Security
Its quite possible that this is not an original idea, but its something that occurred to me while we were discussing presentation planning for the year at the most recent OWASP NoVA chapter meeting. To me, application security can be neatly divided into three key domains: Architecture, Secure Coding, and Testing. Each of these domains represents a distinct set of practices that need to be addressed to have a truly complete appsec program.
What I find fairly interesting about these domains is that theyre not always all considered, whether it be in a software security program, or a Computer Science curriculum, or in contributions from key organizations like OWASP. In fact, it seems that Architecture, in particular, doesnt get much love at all, while a nominal amount of time is spent on secure coding , and while the lions share of time is dedicate to the development of tools for testing.
ArchitectureWhen I say architecture here Im really using the term loosely. In building construction, it is the job of architects to understand and define the requirements, and then translate them into a design that not only takes into consideration the customers vision, but that also makes sound decisions about structure, support, stability, and so on.
Tags:
Read Also: How Much For A Domain Name Per Year
Domain : Physical Security
A commonly overlooked domain, physical security refers to all the controls that should be applied to the physical hardware within our purview:
- Do we have fencing around our facility that forces individuals to enter and exit at the appropriately controlled point?
- Do we have security guards posted at every entrance to our organization?
- Are we securing the data center to only allow physical access to our servers to the authorized individuals?
- Do we have the proper HVAC system in place?
You May Like: How To Buy Cheap Domain Names
Domain : Business Continuity
This domain of cybersecurity focuses on restoring business operations after a catastrophic event, such as a natural disaster. This includes disaster recovery and business continuity plans and procedures. Of course, we should also make sure were periodically reviewing these plans as well as testing them.The business continuity domain revolves around understanding which functions of the organization are vital to the survival of that organization. Once weve identified these critical functions and associated systems, we should put in place procedures to ensure they are operable as soon as possible, with as little data loss as possible, in the event of catastrophic failures.
Read Also: Cost To Buy A Domain
Examples Of Information Security In The Real World
There are many ways to implement information security in your organization, depending on your size, available resources, and the type of information you need to secure. Below are three examples of how organizations implemented information security to meet their needs.
DLP at Berkshire Bank
Berkshire Bank is an example of a company that decided to restructure its DLP strategy. The company wanted to gain access to more detailed reporting on events. Their old system only provided general information when threats were prevented, but the company wanted to know specifics about each event.
To make this change, Berkshire Bank adopted Exabeam solutions to provide managed DLP coverage. This coverage included improved visibility into events and centralized DLP information into a single timeline for greater accessibility. With this enhanced information, Berkshires security team can investigate events better and take meaningful preventative action.
SOC at Grant Thornton
Grant Thornton is an organization that partnered with Exabeam to improve its SOC. The company sought to improve its ability to protect system information and more effectively achieve security goals. Through partnership, Grant Thornton created a data lake, serving as a central repository for their data and tooling.
Incident Response at WSU
Don’t Miss: How To Sell Website Domain
Data Protection Laws In The European Union : The Gdpr
The most known privacy law in the EU is the General Data Protection Regulation . This regulation covers the collection, use, storage, security and transmission of data related to EU residents.
The GDPR applies to any organization doing business with EU citizens, regardless of whether the company itself is based inside or outside the European Union. Violation of the guidelines may result in fines of up to 4% of global sales or 20 million Euro.
The main goals of the GDPR are:
- Setting the privacy of personal data as a basic human right
- Implementing privacy criteria requirements
- Standardization of how privacy rules are applied
GDPR includes protection of the following data types:
- Personal information such as name, ID number, date of birth, or address
- Web data such as IP address, cookies, location, etc.
- Health information including diagnosis and prognosis
- Biometric data including voice data, DNA, and fingerprints
- Private communications
- Cultural, social or economic data