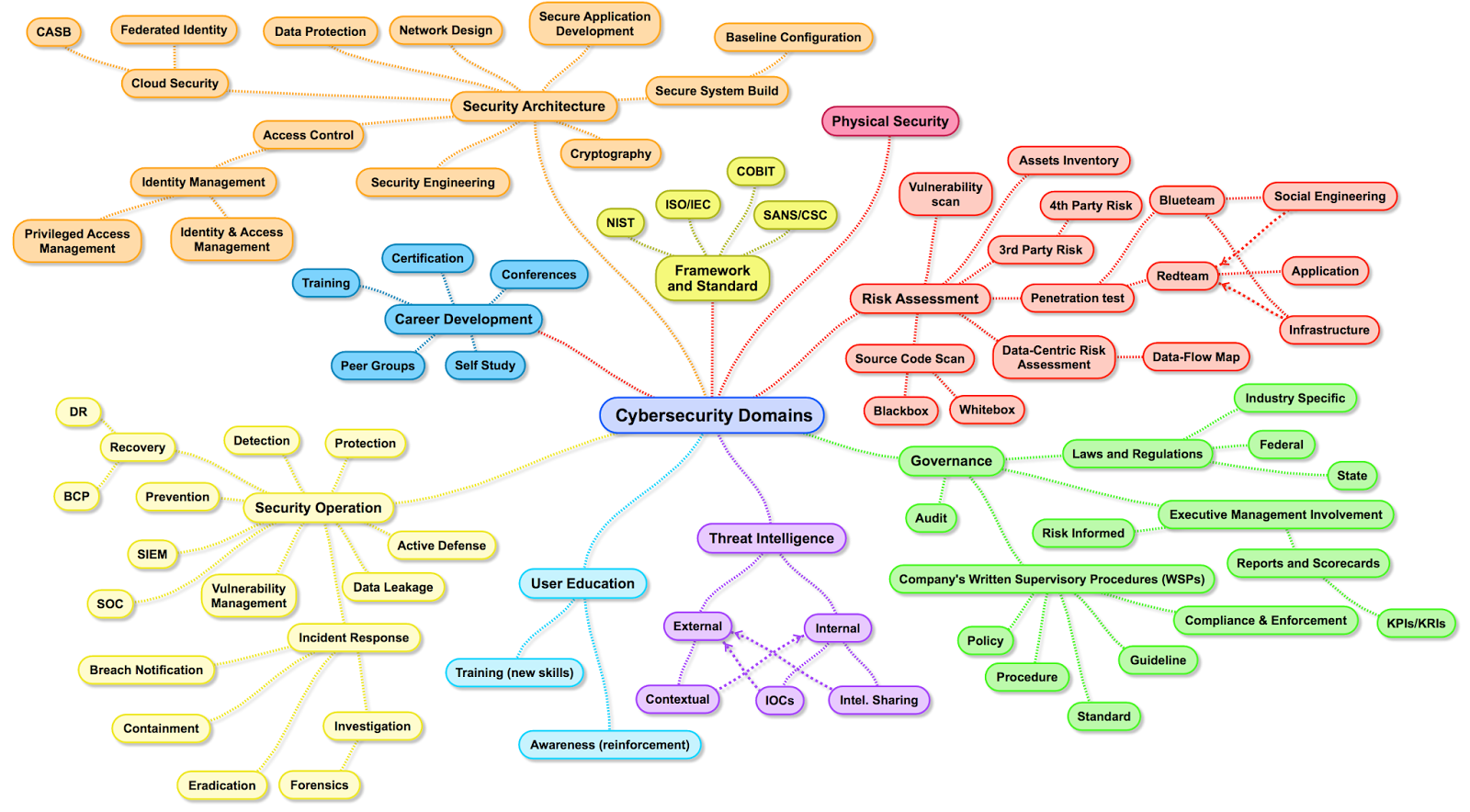
The Cissp Domains And Cbk: An Overview
If you want to climb the IT career ladder, you should consider getting certified. One of the most popular and respected certifications is the Certified Information Systems Security Professionals . Developed and maintained by the international non-profit organization ², CISSP validates a professionals skills and experience in implementing and managing security architects for their organization.
The CISSP exam has eight parts, known as domains. You will need to be proficient in each domain to get the certification. In this post, we will break down each of the eight domains, including how much weight they hold in the exam.
But first, lets take a look at the upcoming CISSP exam changes.
Data Protection Laws In The European Union : The Gdpr
The most known privacy law in the EU is the General Data Protection Regulation . This regulation covers the collection, use, storage, security and transmission of data related to EU residents.
The GDPR applies to any organization doing business with EU citizens, regardless of whether the company itself is based inside or outside the European Union. Violation of the guidelines may result in fines of up to 4% of global sales or 20 million Euro.
The main goals of the GDPR are:
- Setting the privacy of personal data as a basic human right
- Implementing privacy criteria requirements
- Standardization of how privacy rules are applied
GDPR includes protection of the following data types:
- Personal information such as name, ID number, date of birth, or address
- Web data such as IP address, cookies, location, etc.
- Health information including diagnosis and prognosis
- Biometric data including voice data, DNA, and fingerprints
- Private communications
- Cultural, social or economic data
Description And Basic Aspects
The basic concept of the protocol is to tie the financial authorization process with online authentication. This additional security authentication is based on a three-domain model . The three domains are:
- Acquirer domain .
- Issuer domain .
- Interoperability domain . It includes the Internet, merchant plug-in, access control server, and other software providers
The protocol uses XML messages sent over SSL connections with client authentication .
A transaction using Verified-by-Visa or SecureCode will initiate a redirection to the website of the card issuer to authorize the transaction. Each issuer could use any kind of authentication method but typically, a password tied to the card is entered when making online purchases. The Verified-by-Visa protocol recommends the card issuer’s verification page to load in an inline frame session. In this way, the card issuer’s systems can be held responsible for most security breaches. Today it is easy to send a one-time password as part of an SMS text message to users’ mobile phones and emails for authentication, at least during enrollment and for forgotten passwords.
The main difference between Visa and Mastercard implementations lies in the method to generate the UCAF : Mastercard uses AAV and Visa uses CAVV .
Don’t Miss: How Much Do Domains Cost Per Year
The Three Domains Of Application Security
It’s quite possible that this is not an original idea, but it’s something that occurred to me while we were discussing presentation planning for the year at the most recent OWASP NoVA chapter meeting. To me, application security can be neatly divided into three key domains: Architecture, Secure Coding, and Testing. Each of these domains represents a distinct set of practices that need to be addressed to have a truly complete appsec program.
What I find fairly interesting about these domains is that they’re not always all considered, whether it be in a software security program, or a Computer Science curriculum, or in contributions from key organizations like OWASP. In fact, it seems that Architecture, in particular, doesn’t get much love at all, while a nominal amount of time is spent on secure coding , and while the lion’s share of time is dedicate to the development of tools for testing.
ArchitectureWhen I say “architecture” here I’m really using the term loosely. In building construction, it is the job of architects to understand and define the requirements, and then translate them into a design that not only takes into consideration the customer’s vision, but that also makes sound decisions about structure, support, stability, and so on.
Tags:
Data Protection Laws In The Usa
Despite the introduction of some regulations, there are currently no federal laws governing data privacy in general in the United States. However, some regulations protect certain types or use of data. These include:
- Federal Trade Commission Actprohibits organizations from deceiving consumers with regard to privacy policies, failure to adequately protect customer privacy, and misleading advertising.
- Childrens Online Privacy Protection Actregulates the collection of data related to minors.
- Health Insurance Portability and Accounting Act regulates the storage, privacy and use of health information.
- Gramm Leach Bliley Act regulates personal information collected and stored by financial institutions and banks.
- Fair Credit Reporting Actregulates the collection, use, and accessibility of credit records and information.
Additionally, the Federal Trade Commission is responsible for protecting users from fraudulent or unfair transactions such as data security and privacy. The FTC can enact regulations, enforce laws, punish violations, and investigate organizational fraud or suspected violations.
In addition to federal guidelines, 25 US states have enacted various laws to regulate data. The most famous example is the California Consumer Privacy Act . The law went into effect in January 2020 and provides protection to California residents, including the right to access private information, request deletion of private information, and opt out of data collection or resale.
You May Like: How To Figure Out Who Owns A Domain
Definition Of Information Security Management System
An ISMS is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes and IT systems by applying a riskmanagementprocess. It can help small, medium and large businesses in any sector keep information assets secure.
The Information Security Management System represents the collation of all the interrelated/interacting information security elements of an organization so as to ensure policies, procedures, and objectives can be created, implemented, communicated, and evaluated to better guarantee an organization‘s overall information security. This system is typically influenced by organization’s needs, objectives, security requirements, size, and processes. An ISMS includes and lends to effective risk management and mitigation strategies. Additionally, an organization’s adoption of an ISMS largely indicates that it is systematically identifying, assessing, and managing information security risks and “will be capable of successfully addressing information confidentiality, integrity, and availability requirements.” However, the human factors associated with ISMS development, implementation, and practice must also be considered to best ensure the ISMS’ ultimate success.
Principle : The Three Security Goals Are Confidentiality Integrity And Availability
All information security measures try to address at least one of three goals:
- Protect the confidentiality of data
- Preserve the integrity of data
- Promote the availability of data for authorized use
These goals form the confidentiality, integrity, availability triad, the basis of all security programs ” rel=”nofollow”> Figure 2.1). Information security professionals who create policies and procedures must consider each goal when creating a plan to protect a computer system.
The CIA triad.
FYI: CIA Triad
The principle of information security protection of confidentiality, integrity, and availability cannot be overemphasized: This is central to all studies and practices in IS. Youll often see the term CIA triad to illustrate the overall goals for IS throughout the research, guidance, and practices you encounter.
Don’t Miss: What To Do After Buying A Domain
Domain : Security Engineering
Security engineering usually refers to two key subdomains: network security and computer operations security. This domain is where your technical expertise is put to use in securing both the network and hosts from attacks. Its in this domain that we lump the following:
- Firewalls
- Intrusion detection and prevention systems
- Host-based security tools
- Email filtering
- Vulnerability scanning
Domain : Business Continuity
This domain of cybersecurity focuses on restoring business operations after a catastrophic event, such as a natural disaster. This includes disaster recovery and business continuity plans and procedures. Of course, we should also make sure were periodically reviewing these plans as well as testing them.The business continuity domain revolves around understanding which functions of the organization are vital to the survival of that organization. Once weve identified these critical functions and associated systems, we should put in place procedures to ensure they are operable as soon as possible, with as little data loss as possible, in the event of catastrophic failures.
Read Also: Cost To Buy A Domain
Examples Of Information Security In The Real World
There are many ways to implement information security in your organization, depending on your size, available resources, and the type of information you need to secure. Below are three examples of how organizations implemented information security to meet their needs.
DLP at Berkshire Bank
Berkshire Bank is an example of a company that decided to restructure its DLP strategy. The company wanted to gain access to more detailed reporting on events. Their old system only provided general information when threats were prevented, but the company wanted to know specifics about each event.
To make this change, Berkshire Bank adopted Exabeam solutions to provide managed DLP coverage. This coverage included improved visibility into events and centralized DLP information into a single timeline for greater accessibility. With this enhanced information, Berkshires security team can investigate events better and take meaningful preventative action.
SOC at Grant Thornton
Grant Thornton is an organization that partnered with Exabeam to improve its SOC. The company sought to improve its ability to protect system information and more effectively achieve security goals. Through partnership, Grant Thornton created a data lake, serving as a central repository for their data and tooling.
Incident Response at WSU
How To Achieve 360 Cybersecurity Approach By Covering These Three Domains Ie People Processes And Technology
Security threats are constantly evolving and your security measures need to adjust accordingly. You should have strong mechanism to protect your ogragnization with help of People, Process & Technology.
There should be a comprehensive framework to help you & evaluate your current cybersecurity landscape and ensure you have proper protection.
360° Cybersecurity approach : This Approach covers the three main domains of people, process and technology & these three steps-
Step 1 is to identify and assess your current level of threat, risks and protection.
Identify > Threat—-> Risk —-> Strategy —-> Security review.
Step 2 is to take corrective action where gaps are identified.
Protect > People —-> Process —-> Technology.
Step 3 is to monitor the system, respond to threats and incidents and allow you to report to your board and regulators”
Monitor > Real Time —-> Scheduled—-> Unscheduled —-> Security Review.
You May Like: Vistaprint Domain Transfer
Identity And Access Management
Identity and Access Management comprises about 13% of the CISSP exam.
This domain helps information security professionals understand how to control the way users can access data. It covers:
- Physical and logical access to assets
- Identification and authentication
- Integrating identity as a service and third-party identity services
- The identity and access provisioning lifecycle.
What Is A Security Domain

Join the Community
A security domain is a term used to conceptualize any grouping of computers, networks, or information technology infrastructure elements that fall under a specific security protocol. The domain is established as a restricted unit of those elements that then have a single authentication method for access to the elements within the security domain. Given that the term is so conceptual in nature, it can be applied to a wide range of information technology elements such as a collection of web sites, a communications network, a group of computers in a room, and even a combination of any or all of these.
One such example of a security domain is the use of a web access management architecture to handle authorization for a series of websites or web pages. This can be handled in a couple different ways, such as a software agent on the web server or a separate proxy server. With a software agent, each web server has a small software program installed that receives authentication information from another server. The software on the web server intercepts a web request and then checks with the access management server for permission before allowing or denying access to the web site or a specific web page. With a proxy server setup, on the other hand, the proxy server contains the access permissions for the web servers that it guards, intercepts requests to those servers, and only allows requests that meet the proper security criteria.
Read Also: How To Transfer Domain From Wix To Shopify
Using The 14 Domains Of Iso 27001
Organisations arent required to implement all 114 of ISO 27001s controls.
Theyre simply a list of possibilities that you should consider based on your organisations requirements.
Annex A provides an outline of each control. You should refer back to it when conducting an ISO 27001 gap analysis and risk assessment.
These processes help organisations identify the risks they face and the controls they must implement to tackle them.
The only problem with Annex A is that it only provides a brief overview of each control. While this is good for reference use, its not helpful when actively implementing the control.
Thats where ISO 27002 comes in. Its a supplementary standard in the ISO 27000 series, providing a detailed overview of information security controls.
The Standard dedicates about one page to each control, explaining how it works and implementing it.
Security And Risk Management
So security and risk management involve a general understanding.
Also, analysis and risk-mitigating techniques. To determine the team achieves their goal of learning security goals.
So the risk is a major basic in every viewpoint. It is just like information security decisions.
Also, risk management concepts are helping aid each decision. To make effective.
This is the list of the major part of security and risk management.
- Information security within the team
- The triad of information security Confidentiality, Integrity, and Availability
- Security governance policies
- Policies, standards, procedure, and guidelines
- The idea of risk management
You May Like: How Much Is It To Buy A Domain Name
Verifiability Of Site Identity
The system involves a pop-up window or inline frame appearing during the online transaction process, requiring the cardholder to enter a password which, if the transaction is legitimate, their card issuer will be able to authenticate. The problem for the cardholder is determining if the pop-up window or frame is really from their card issuer when it could be from a fraudulent website attempting to harvest the cardholder’s details. Such pop-up windows or script-based frames lack any access to any security certificate, eliminating any way to confirm the credentials of the implementation of 3-DS.
The Verified-by-Visa system has drawn some criticism, since it is hard for users to differentiate between the legitimate Verified-by-Visa pop-up window or inline frame, and a fraudulent phishing site. This is because the pop-up window is served from a domain which is:
- Not the site where the user is shopping
- Not the card issuer
- Not visa.com or mastercard.com
Implementation of 3-D Secure sign-up will often not allow a user to proceed with a purchase until they have agreed to sign up to 3-D Secure and its terms and conditions, not offering any alternative way of navigating away from the page than closing it, thus suspending the transaction.