Why Resilience Is Important
In an environment with just a single Domain Controller, failures can lead to some major issues. The problems can be summed up in a few words: expense, inefficiency, and inconvenience.
For businesses that have only one Domain Controller, failure will lead to big-time consequences, such as:
- Remote workers will be unable to authenticate
- Application services that use AD authentication will stop functioning
- Business critical systems relying on the above services will also falter, which may include the ERP system
- If the AD does DHCP and DNS, these protocols will also fail, which means internet routing will stop working
- New workstations logging on to the systems will not be able to get their IP addresses, which means they will require manual assignment.
These are things that not only inconvenience and delay team members and processes, but also delay the actual work of getting the servers up-and-running again.
In many cases, it takes days for the system environment to get back into the full swing of things, and that downtime can cost a business a significant amount of time and money.
Unfortunately, the majority of businesses that find themselves in this position discovertoo latethat there is no usable backup at the infrastructure level that they can use to restore their Domain Controller.
With their one and only DC gone and the Active Directory all but broken, they basically will be forced to spend days reconstructing the server from scratch.
How Can Cloud Directory Services Help
Previously, IT infrastructure was largely Microsoft-based, so companies relied entirely on Microsofts Active Directory for access management. But now, as IT networks are increasingly shifting to the cloud, cloud-based access management options have also emerged. Cloud directory services are a modem alternative to the traditional, on-premises Active Directory. Delivered through the cloud, these services can be used to build an identity management system from scratch or extend your companys Active Directory services across cloud and on-premises environments.
Cloud directory services provide similar functionality to Microsoft Active Directory services along with the added security, scalability, and convenience of the cloud. For companies running on a single domain controller, cloud directory services, such as Azure Directory, make it extremely simple and quick to set up a secondary domain controller in the cloud. With a secondary domain controller within the Azure cloud, your Network infrastructure can enjoy business continuity and resilience at a very low cost.
The Benefits Of A Domain Controller
Benefits of a domain controller include:
- Domain controllers that support protected authentication and transport protocols increase the security of the authentication process.
- Domain controllers enable smooth interaction with directory services like Microsoft AD by checking for access to file servers and other network resources.
- Across company networks and the wide-area network, replicated and distributed domain controllers impose security policies and fend off any unwanted access.
- Companies may authenticate all directory service requests using a centralized domain controller for domain controller administration.
Also Check: What Are Net Domains Used For
Why Domain Controllers Are An Important Part Of Active Directory
Domain controllers provide the physical storage for the AD DS database. In addition, they also provide services that allow enterprises and IT pros to manage their servers, computers, laptops, users, printers, and other applications. They are vitally important to your network and need to be secured. A malicious user, if they can take control of a DC, could wreak havoc on your Friday afternoon by wiping out your AD database.
How Msps Should Ensure Security Of Their Dcs
Given the high-value and high-risk of the DCs and therefore the AD, its absolutely critical that you take the necessary steps to protect it. Here are a couple of strategies you can use:
- Limit physical and remote access to your DCs
- For virtual domain controllers, run them on dedicated physical hosts
- Continually monitor and audit your DC
- Implement robust security protocols, including stringent authentication processes like multi-factor authentication and unique or complex password requirements
- Minimize the vulnerability of your DCs and AD by granting domain admin status to only a select few users
- Ensure your DCs always have empty disk space and limit the other services that your DC is running
- Block internet access on your DCs
- Run all DCs on the most up-to-date OS
Sounds difficult? It doesnt have to be, as Ateras Network Discovery makes it easy to proactively maintain and audit your clients networks by scanning your customers workgroups and DC networks. Try it for free with our free trial.
You May Like: How To Verify My Domain
Roll Out Software Simultaneously To Different Groups
You dont need to go to each workstation and manually install the software your employees need if you have a domain controller.
Schenk shared, Lets say I want to deploy software. I can use something called Group Policy Objects or GPOs to deploy certain types of software or configuration changes to my group of machines.
He also mentioned you could control the presentation of your companys workstations.
Lets say I want to remove certain kinds of menus from Windows 10, he said, I can set up a user profile, company profile, or preferences that allow these things to go ahead and be streamlined and hidden for security reasons.
This standardization process would take an unreasonable amount of time for your IT team without a domain controller.
Get Started With Domain Joining With Instasafe
Domain Joining and Controllers come with their own perks and vulnerabilities. While they strengthen your network and ensure maximum user data security and protectionchoosing the right service and implementing domain controllers is paramount.
If you need a service to connect your remote employee devices to your corporate domain securely, check out our InstaSafe solutions. Get domain joining to ensure compliance with updated security protocols, push group security policies to remote devices, and enable maximum control over security patches and updates. Book a demo today to learn more!
Recommended Reading: Where To Buy Gg Domains
Active Directory Reporting With Solarwinds Access Rights Manager
Generating reports on Active Directory is essential for optimizing performance and staying in accordance with regulatory compliance. One of the best Active Directory reporting tools is SolarWinds Access Rights Manager . The tool has been created to increase visibility into how directory credentials are used and managed. For example, you can view accounts with insecure configurations and credential abuse that could indicate a cyber attack.
Using a third-party tool like SolarWinds Access Rights Manager is beneficial because it provides you with information and features that would be much more difficult or impossible to access through Active Directory directly.
As well as generating reports you can automatically delete inactive or expired accounts that cybercriminals target. SolarWinds Access Rights Manager starts at $3,444 . There is also a 30-day free trial version that you can download.
See also:Access Rights Management
The Main Function Of A Domain Controller
During the research for this article, I often came across the question: What is a domain controller in Active Directory?. Its a fun question because the question should be What is Active Directory on a domain controller?. The reason for this is that the domain controller is the server where Active Directory is installed. So, without a domain controller , there is no Active Directory .
A domain controller is a role that you can assign to a Windows server. You do this when you are installing the service AD DS, which stands for Active Directory Domain Services. Depending on the version of Windows Server, you can choose a domain controller to be primary or not, more on that later.
Recommended Reading: What Does It Mean To Register A Domain
What Is A Domain Controller And Why Would I Need It
User authentication and authorization are critical for protecting your network infrastructure. It ensures that only trustworthy and relevant users can access the network. A Windows Server domain logically groups users, PCs, and other objects in a network, while a domain controller authenticates access requests to the domains resources. It also stores information about user accounts and devices and enforces security policies.
Learn the important role of a domain controller within a network infrastructure, and set it up with fault tolerance.
Why Can Domain Controllers Be A Risk
Given that DCs are a critical gatekeeper to your domain, theyre also a prime target for cyber attacks. Their crucial role in authenticating users and granting access to your networks make them highly liable to being preyed on.
A successful breach of your DC can lead to serious damage to your AD DS database, security leaks, and compromised user credentials and data. Should your AD forest be compromised, youll be unable to use it again unless you have a good and reliable backup.
Thats why MSPs should ensure that they implement sturdy cybersecurity measures to protect their domain controllers.
Another issue to consider is just how dependent your networks are on your DCs uptime. For this reason, its advisable that your DCs are dedicated solely to domain services. This is because running any other services risks slowing down or crashing the system.
Read Also: When Was A Domain Purchased
Dynamic Host Configuration Protocol
The DHCP is a network management protocol used for dynamic address allocation. The protocol relies on the DHCP server to automatically provision IP addresses, default gateway, and other information to DHCP clients. Active Directory depends on a DHCP server to start responding to client requests.
When a client using DHCP connects to a network, it instantly sends a DHCP discovery to find the server, which in turn sends a DHCP offer with an available IP address.
You May Like: Shopify Transfer Domain
Domain Controller Best Practices
Implement principles of least privilege in AD roles and groups: Domain controllers work on the principle of least privilege, which means they review all the necessary permissions granted to employee roles for accessing data and applications. It also ensures employees have a minimal level of access to perform their duties.
Use real-time auditing and alerting: Its important to report unusual or excessive login attempts. You should provide your domain controller full auditing and alerting capabilities to help ensure secure internal or external access. This also helps you demonstrate adherence to compliance requirements such as SOX, HIPAA, PCI.
Ensure data backup and recovery: Data backup is crucial and must be performed regularly. Practice data backup and disaster recovery processes for faster recovery.
Centralize and Automate: Its important to collect reports, reviews, and user controls in one place for issue resolution. You can also use tools with automated workflows for reconciling issues and ending alerts.
Standardize your domain controller configuration for reuse: Setting up a stable domain controller doesn’t mean your network is secure. Attackers can still hack your domain controller and try escalating privileges. Use deployment tools, configuration management tools, access rights management tools, and more to capture security-related information, boot settings, and hardware configurations.
Read Also: How To Copyright A Domain Name
What Are The Types Of Domain Controllers
There are two major types of a Domain Controllerread-only and read-write.
- Read-only: The read-only Domain Controller comprises a copy of the AD DS database, which is read-only.
- Read-write: A read-write Domain Controller comes with the ability to read and write to the AD DS database.
With that in mind, lets also understand what domain joining is and how it differs from Domain Controllers.
Path To The Domain Controller
The premise here is aligned with the assume breach philosophy which implies that a threat actor may already have unauthorized access to your systems or network, albeit possibly with lower-level privileges. For example, this could be the compromise of a user account via phishing that may, in turn, lead to business email compromise . This will also imply that the threat actor is more than likely trying to work their way to a higher privileged account and subsequently crown jewel system such as the domain controller.
Lets look at a hypothetical attack flow following this pattern:
The initial attack involves a phishing email to an employee. This phishing attack contains a link to a fake Office 365 OneDrive login which the employee falls for. In conjunction with javascript execution and in some cases vulnerability, such a link automatically runs a memory-only malware leveraging Windows Powershell. This then leads to a reverse shell command and control backdoor from the compromised users Windows laptop back to the attacker. This is the starting point for this articles assume breach premise.
The attack up to this stage will be mostly automated so the attacker will likely get a C& C notification about a new shell and therefore a new compromised machine. They are also going to be mainly oblivious of the full details of the compromised system such as user accounts, privileges and network resource access. This is where the ATT& CK Discovery Phase is important to an attacker.
Don’t Miss: How To Find Domain Registrar
Troubleshooting The Domain Locator Process
To troubleshoot the domain locator process:
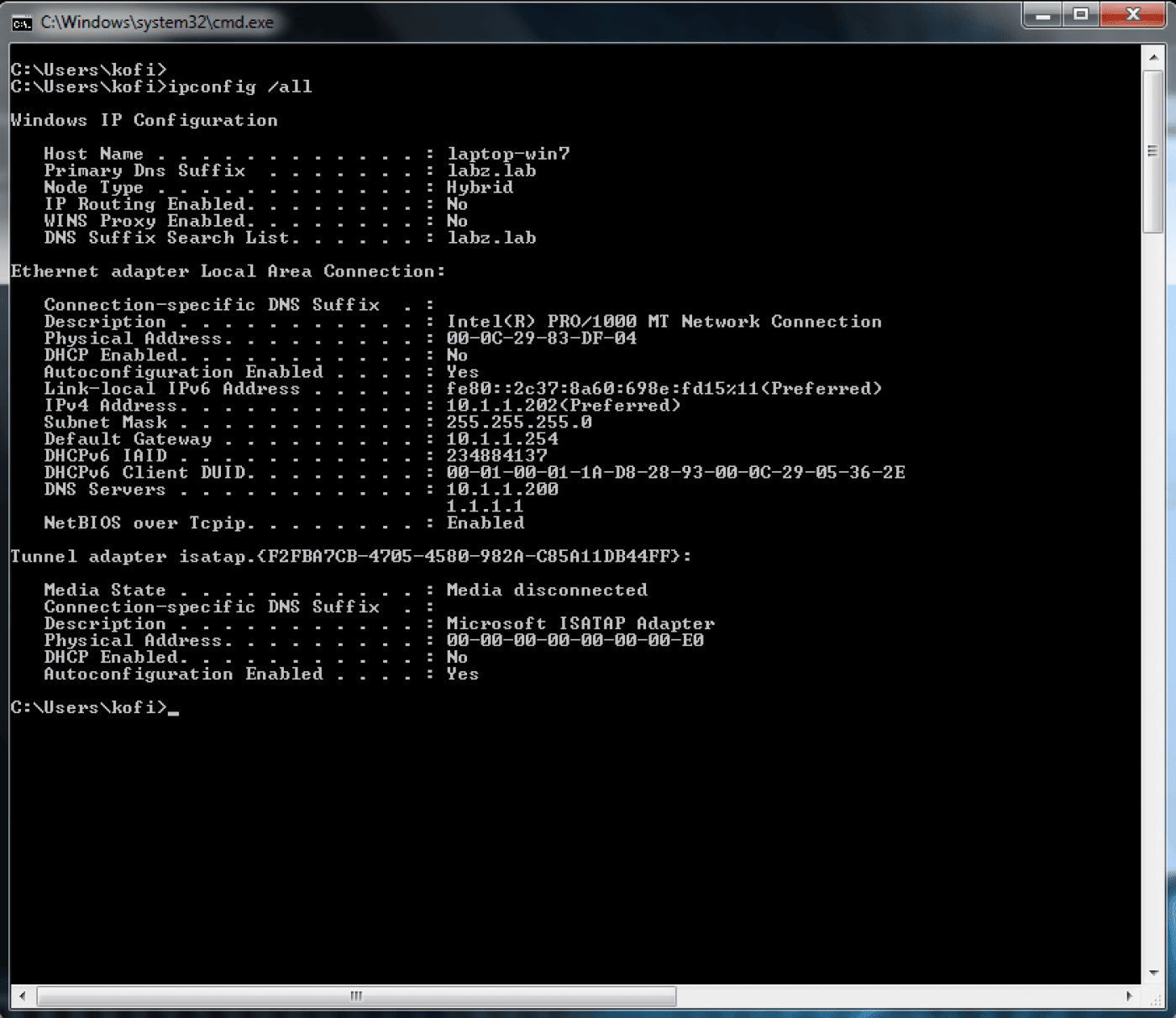
Check Event Viewer on both the client and the server. The event logs may contain error messages indicating that there’s a problem. To view Event Viewer, select Start, point to Programs> Administrative Tools, and then select Event Viewer. Check the System log on both the client and the server. Also check the Directory Service logs on the server and DNS logs on the DNS server.
Check the IP configuration by using the ipconfig /all command at a command prompt.
Use the Ping utility to verify network connectivity and name resolution. Ping both the IP address and the server name. You may also want to ping the domain name.
Use the Netdiag tool to determine whether networking components are working correctly. To send detailed output to a text file, use the following command:
netdiag /v > test.txtReview the log file, looking for problems, and investigate any implicated components. This file also contains other network configuration details.
To fix minor problems, use the Netdiag tool with the following syntax:
netdiag /fix.
Use the nltest /dsgetdc:domainname command to verify that a domain controller can be located for a specific domain.
If either of these commands doesn’t succeed, use one of the following methods to reregister records with DNS:
What Is The Difference Between A Domain And A Domain Controller
Every computer workstation has its own user accounts, called local accounts, that are used to log in to that particular machine. However, these accounts are not designed to log in to a network for two reasons. First, network accounts need to be portablea user should be able to access the network from any workstation. Second, account configuration needs to be controlled from a central location. Otherwise, whenever account privileges change, system administrators would need to separately configure accounts on each local device.
This is where a domain comes in. A network domain centralizes user accounts so they can be more easily administered and enables users to log in to the network from any given machine. Within a domain, a domain controller is used to regulate user account access to the network.
Don’t Miss: How To Change My Google Domain Name
Do You Need A Domain Controller: Advantages And Drawbacks
Irrespective of your organisation or business sizeyou need a Domain Controller to improve your networks security if you save your customers data and login credentials on your enterprise network.
Here are the benefits of a Domain Controller for your organisation network:
- Centralises user data management for efficient organisation and data storage.
- Makes resource sharing for files and printers a breeze.
- Simplifies network administrative workload.
- Facilitates and provides more control over users settings and entitlements.
- Maximises and ensures high network and data security.
- Enables user data encryption.
- Enables Federation configuration for redundancy .
- Increases collaborative possibilities within the domain.
- Easier to distribute and replicate across large networks.
- Easier to harden and lockdown for improved security.
Here are the limitations or cons of a Domain Controller :
- Comes with the potential to be hacked and become an easy target for cyberattacks.
- You must ensure users and the Operating Systems stability and security.
- Its important to check for hardware and software requirements and keep them up-to-date.
- Your network depends on the Domain Controllers uptime.
What Are The Best Practices For Protecting Domain Controllers
Glad you asked! Its essential to remember that any server running AD DS is a top target for cyberattacks. A hacker who compromises one of your domain controllers is well-positioned to achieve whatever nefarious goals they have, from stealing your most valuable data to sabotaging critical business processes. And, as Microsoft points out, Depending on an attackers preparation, tooling, and skill, modification or even irreparable damage to the AD DS database can be completed in minutes to hours, not days or weeks.
Therefore, its essential to protect your domain controllers like Fort Knox. In particular:
Also Check: Transfer Godaddy Domain To Wix
Also Check: Can I Buy A Domain On Wix
Woman Jumps In Front Of Train Today
24) What do you understand by domain trees and forests? Domain trees and forests both are two important concepts of Active Directory. A domain tree is a collection of one or more domains that share a common namespace. For example, jobs.career.com and career.com both domains are a part of the career.com domain tree. Domain Controllers rely on SRV records registered in the DNS Server to perform important functions such as replicating changes and allow Active Directory clients to locate domain controller services. Any application that uses SRV records to find a domain controller will fail if SRV records for domain controllers are not registered. Active Directory domain services Hierarchical structure explained. Alright so lets talk a bit about Active Directorys hierarchical structure. Essentially, the hierarchical structure of an AD is comprised of forests, trees, domains, and organizational units .
Other Domain Controller Implementation Options
The following options are available when setting up a domain controller with AD:
- Domain Name System server: The domain controller can be configured to function as a DNS server. Dell recommends configuring at least one domain controller as a DNS server.
- Global Catalog capabilities: The domain controller can be configured to use Global Catalog, which enables the controller to return AD information about any object in the organization, regardless of whether the object is in the same domain as the domain controller. This is useful for large enterprises with multiple AD domains.
- Read only domain controller : Domain controllers used in branch offices or in other circumstances where network connectivity is limited can be configured as read-only.
- Directory Services Restore Mode : DSRM provides the option to do emergency maintenance, including restoring backups, on the domain controller. A DSRM password must be configured in advance.
Read Also: Is Local A Valid Domain