Securing The Seven Domains Of It Infrastructure
When a business environment is opened up to the Internet, many risks can be introduced into the organization. These risks must be identified and managed in order to defend and protect the organization from attack. Additionally, the people within the organization can intentionally or unintentionally introduce risk simply by performing their daily job duties. When these duties are performed in the absence of clear direction from policy and best practices, risk can grow exponentially. The following information will help demonstrate the importance of securing the seven domains of IT infrastructure.
User Domain
The User Domain represents a great weakness within the IT infrastructure. This domain includes any end-user accessing information at the organization. With almost 90% of cyber-attacks caused by human error or behavior , this domain needs strong scrutiny. The following risks have been identified within this domain:
-
Employees that fail to lock their computers when getting up from their desks.
-
Employees that leave sensitive company information on their desks.
-
Limited IT security knowledge by employees can lead to the introduction of malware and social engineering schemes.
-
Employee negligence from a lack of policy can lead to legal ramifications for the business.
Workstation Domain
LAN Domain
-
Flat network designs lack security.
-
IT Employees may lack the experience, or the time, in designing and maintaining a secure network.
-
Lack of security policy governing the network.
Policies For The Seven Domains Of A Typical It Infrastructure
User Domain policy Clean desk policy would be a user domain policy. It would ensure that confidential hard copies of data arent left in plain view.
Workstation Domain This domain would have an encryption policy. This would ensure that all PCs, laptops, and mobile devices are safeguarded with full-disk encryption and ensure confidentiality of the organizations data.
LAN Domain Configuration Change Control policy. This policy would enforce the documentation of baseline hardened configurations of all devices on the Local Area Network and monitoring and tracking of any changes. This would prevent authorized changes and prevent vulnerabilities from creeping into the LAN domain.
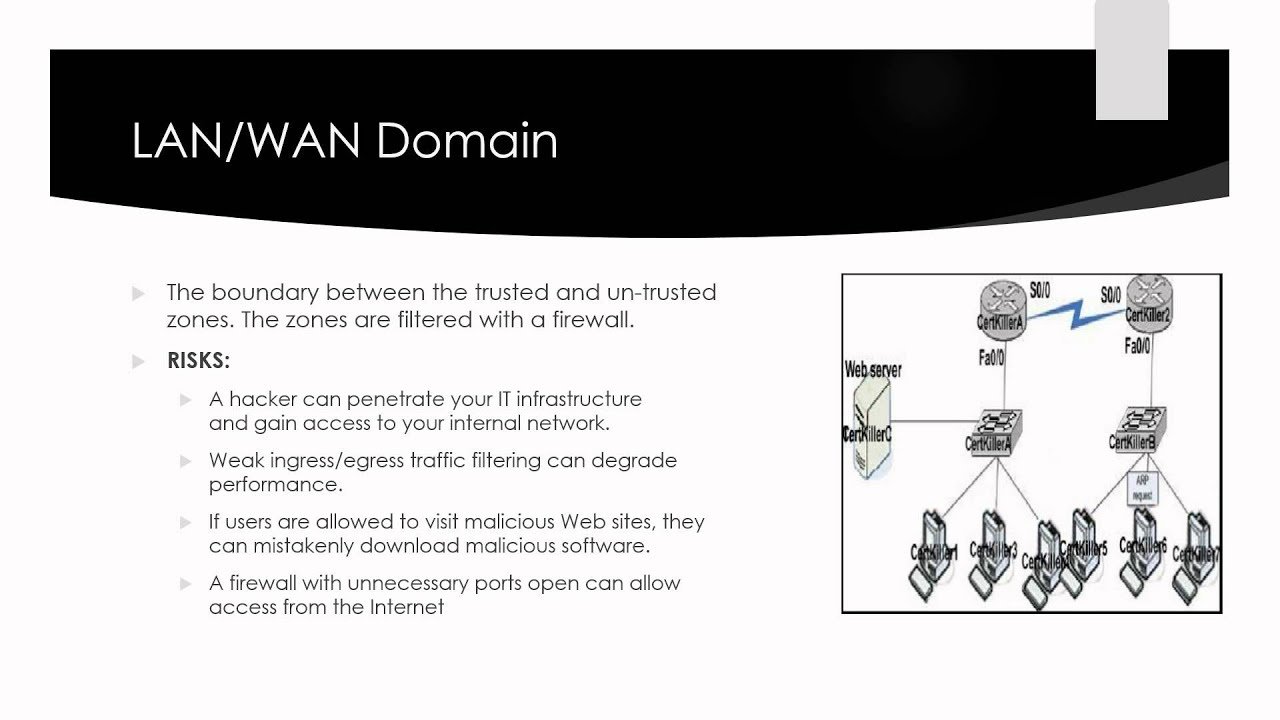
LAN to WAN Domain It would have a perimeter firewall policy. This policy would enforce the implementation and configuration of a perimeter firewall, as well as ensure that its logs are monitored diligently.
WAN Domain An Access Point policy would be important for this domain to root out security concern that can occur when two or more LANs are connected. It can handle the bandwidth, traffic segmentation, and address range issues.
Remote Access Domain The VPN policy would be typical for this domain. This ensures all remote connections are secure, through an encrypted tunnel, and maintain confidentiality and integrity of data in transit.
The Seven Domain Of A Typical It Infrastructure
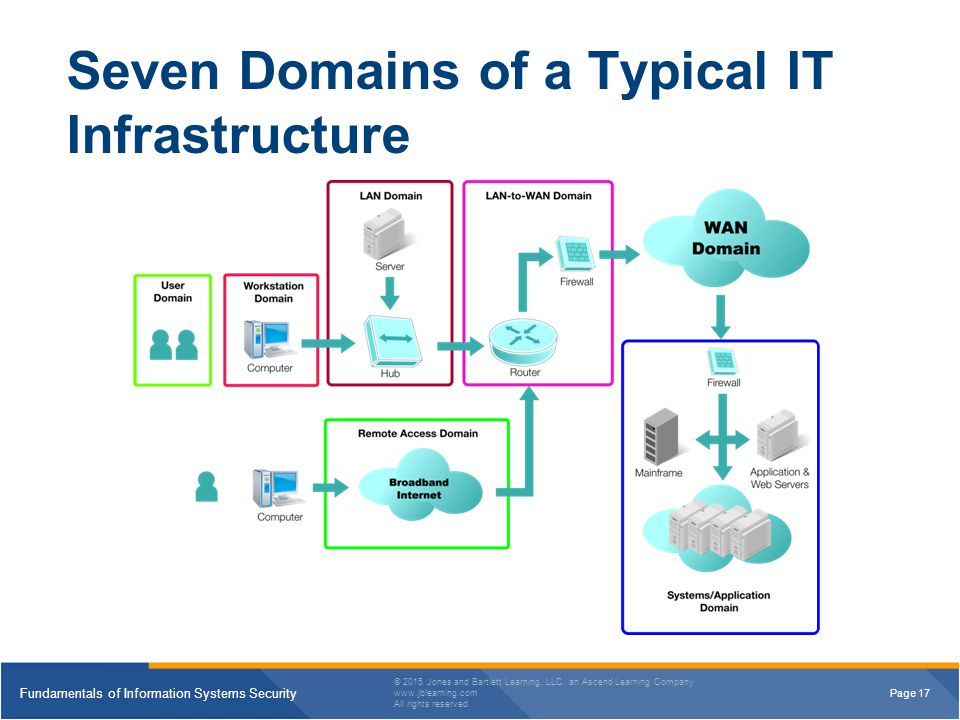
Seven Domains of IT Infrastructure Seven domains can be found in a typical IT infrastructure. They are as follows: User Domain, Workstation Domain, LAN Domain, LAN-to-WAN Domain, Remote Access Domain, WAN Domain, and System/Application Domain. Each of these domains is viewed as portals for attackers if countermeasures are missing or fail. It is very imperative for businesses to protect each of these seven domains. It only takes one unprotected domain for an attacker to gain access to private data.
- User Domain.The User Domain covers all theusers that haveaccess to the other six domains.
RISKS:
- Workstation Domain.A computer of an individual user where the production takes place
RISKS:
- LAN Domain.Contains all of the workstations,hubs, switches, and routers. TheLAN is a trusted zone
RISKS:
Also Check: How To Tell Who Owns A Domain Name
This Problem Has Been Solved
Create a security management policy that addresses themanagement and the separation of duties throughout the sevendomains of a typical IT infrastructure. You are to define what theinformation systems security responsibility is for each of theseven domains of a typical IT infrastructure. From this definition,you must incorporate a definition for the separation of duties intothe Procedures section of the policy definition template that youwill fill out later in this step.
The scenario you are to work with is for the mock Lone StarCredit Union/Bank:
The organization is a regional Lone Star Credit Union/Bank thathas multiple branches and locations throughout the region.
Online banking and use of the Internet are the banks strengths,given its limited human resources.
The customer service department is the organizations mostcritical business function.
The organization wants to be in compliance with theGramm-Leach-Bliley Act and IT security best practicesregarding its employees.
The organization wants to monitor and control use of theInternet by implementing content filtering.
The organization wants to eliminate personal use oforganization-owned IT assets and systems.
The organization wants to monitor and control use of the e-mailsystem by implementing e-mail security controls.
The organization wants to implement this policy for all the ITassets it owns and to incorporate this policy review into itsannual security awareness training.
Lone Star Credit Union
Project Requirements And Analysis Essay
be issued to them at the time of registration to the library. Once a user has registered he will be issued a smart card that will contain security certificates that control the users’ rights on the network, and also serve as a tracking hit for all typical library resources checked out. All 8 Dell Precision Workstation 490 Desktop – 64bit workstations will have this software installed on it and will not allow computer usage till a smart card has been inserted. Also included into phase 2 is 2 Dell
You May Like: How To Find Email Domain And Server
The Seven Domains Of A Typical It Infrastructure
892446
User – The User Domain is the critical backbone of our network and we must pay close attention to user activity and shape user behavior on our network. I list this as a high priority due to the fact that it is the one that will most likely open up threats on our network from file downloading and surfing the web. My proposal for a solution for this would be to restrict web browsing to only required users. This will allow us to focus our concentration on those users, monitoring for potential network vulnerabilities.
First we will need to ensure the safety of our equipment from tampering. We should have all switches and sensitive equipment Devices) in a room that is locked at all times. If available, we can use a card access system to monitor employees that gain access to this portion of our network. Wireless connections open our network to potential threats. We should do everything possible to limit the number of allowed wireless devices on our network. I suggest that we enforce a policy of a primary and secondary wireless network.
Order custom essay The seven domains of a typical IT infrastructure with free plagiarism report
Best Practice Active Directory Design For Managing Windows Networks
Some services that can be layered on Active directory are: Group Policy Exchange 2000 Integrated public key infrastructure services Domain-based DFSSpecial Considerations for Branch Office DeploymentsMicrosoft has identified a number of special considerations for deploying Active Directory in branch office environments. The characteristics of a branch office
Recommended Reading: Transfer Wix Domain To Squarespace
Developing A Risk Mitigation Plan Outline For An It Infrastructure 19558769
Prepare a Lab Report file which covers the below mentioned points:
1) Identify the scope of IT risk-mitigation plan focusing on the seven domains of a typical IT infrastructure.
2) Align the major parts of an IT risk-mitigation plan in each of the seven domains of a typical IT infrastructure.
3) Define the tactical risk-mitigation steps needed to re-mediate the identified risks, threats, and vulnerabilities commonly found in the seven domains of a typical IT infrastructure.
4) Define procedures and processes needed to maintain a security baseline definition for ongoing risk mitigation in the seven domains of a typical infrastructure.
5) Create an outline for an IT risk-mitigation plan encompassing the seven domains of a typical IT infrastructure.
Please follow this Hands-on steps to prepare the Lab Report File. This should be followed in a step by step procedure while building the Lab report.
1) Create a new word document.
2) Review the seven domains of a typical IT infrastructure.
3) Using the following table, review the results of your assessments in performing a Qualitative Risk Assessment for an IT infrastructure lab in this lab manual. In addition, review the results of how you categorized and prioritized the risks for the IT infrastructure in that lab:
4) In your lab report file, organize the qualitative risk assessment data according to the following:
6) Read the article titled Risk Impact Assessment and Prioritization
· Executive summary
Analyze The Seven Security Domains Of A Typical It Infrastructure And Determine Which Two Of The Seven You Would Implement First For A Nationwide Bank Explain Your Rationale For Your Choice
Security Layers Please respond to the following:
Security Layers Please respond to the following:Discussion 1Analyze the seven security domains of a typical IT infrastructure and determine which two of the seven you would implement first for a nationwide bank. Explain your rationale for your choice.Explain the concept of incorporating redundancy throughout and corporate network. There are also times when redundancy can produce a false sense of security primarily based on how it is incorporated in a design. Explain such a case and how to overcome the falsehood.Discussion 212345Protecting the System Please respond to the following:
Describe some drawbacks to hardening a computer system which is currently in a production environment and how the fears associated with those drawbacks can be put to rest. Propose how you would proceed in this environment.Assess the importance of implementing Authentication, Authorization, and Accounting as a security measure. Explain the value AAA holds throughout an organizations network. Identify the layers of the open systems interconnection model that are influenced by a typical AAA implementation or solution.
NSWER
| Paper Title |
Institutional Affiliation
Security Layers
You May Like: How To Transfer Squarespace Domain To Godaddy
In The Seven Domains Of A Typical It Infrastructure
Overview
In this lab, you defined the purpose of an IT risk management plan, you defined the scope for an IT risk management plan that encompasses the seven domains of a typical IT infrastructure, you related the risks, threats, and vulnerabilities to the plan, and you created an IT risk management plan outline that incorporates the five major parts of an IT risk management process.
1. What is the goal or objective of an IT risk management plan?
2. What are the five fundamental components of an IT risk management plan?
3. Define what risk planning is?
4. What is the first step in performing risk management?
6. What practice helps address a risk?
7. What ongoing practice helps track risk in real time?
8. True or False: Once a company completes all risk management steps , the task is done.
9. Given that an IT risk management plan can be large in scope, why is it a good idea to develop a risk management plan team?
10. In the seven domains of a typical IT infrastructure, which domain is the most difficult to plan, identify, assess, treat, and monitor?
11. Which compliance laws or standards does the health care organization mentioned in the HandsOn Steps have to comply with ? How does this impact the scope and boundary of its IT risk management plan?
12. How did the risk identification and risk assessment of the identified risks, threats, and vulnerabilities contribute to your IT risk management plan outline?
16. What is the purpose of a risk register?
What Is System Application Domain
An application domain is the segment of reality for which a software system is developed. It is the background or starting point for the actual-state analysis and the creation of a domain model. An application domain can be an organization, a department within an organization, or a single workplace.
Read Also: How To Access Google Domain
What Is Domain Infrastructure
What are the seven domains?
What is the most important part of IT infrastructure?
Why do organizations have acceptable use policies AUPs )?
Why is the remote access domain the most risk prone of all in a typical IT infrastructure?
What are three risks and threats of the user domain?
What is the most important risk mitigation requirement you uncovered and want to communicate to executive management?
The Seven Domains Of It Infrastructure
Extracts from this document…
Introduction
Seven Domains of IT Infrastructure Seven domains can be found in a typical IT infrastructure. They are as follows: User Domain, Workstation Domain, LAN Domain, LAN-to-WAN Domain, Remote Access Domain, WAN Domain, and System/Application Domain. Each of these domains is viewed as portals for attackers if countermeasures are missing or fail. It is very imperative for businesses to protect each of these seven domains. It only takes one unprotected domain for an attacker to gain access to private data. The User Domain is comprised of individuals that are often not aware of the tricks of attackers. For example, networks usually have strong passwords that one must know in order to gain access to the Internet. Nevertheless, social engineers can persuade individuals to give out personal information such as passwords and other types of private information. …read more.
Middle
This student written piece of work is one of many that can be found in our AS and A Level Computer Science section.
Also Check: How To Sell Domain Names For Profit
What Is The Role Of It Infrastructure Services
The purpose of IT infrastructure management is to provide structure and control of the functions responsible for diverse technical operations which generally involve hardware, software, and networking in both physical and virtual environments. The main goal is to minimize downtime and maintain business productivity.
Cloud Computing : A Key Differentiator And Competitive Edge Between Cloud Essay
cloud computing.Index Terms – Cloud, Security, Security challenges, Cloud computing.I. INTRODUCTION The term cloud was coined from the computer network diagrams which use it to hide the complexity of infrastructure involved. cloud computing provides software, platform and infrastructure as a service. its main features include resource pooling, rapid elasticity, measured service, on-demand self service and broad network access. so, a cloud is a collection of hardware and software that runs in
Read Also: Connect Godaddy To Squarespace
Main Body 7 Domains Of An It Infrastructure Essay
Here are some of the most important factors involved with designing an IT infrastructure for your company or organization:
1. Hardware Design
- The number of servers required
- The number of employees to be supported
- Current hardware used
2. Software Design
- What software will be needed for the infrastructure?
- How important is it that all of these needs are met by a single vendor or multiple vendors?
3. Network Design
The network design should also take into account security management and data center operations. See those sections for more information.
4. Security Management
- How secure does your company need the system to be? What kinds of attacks are you looking to defend against? Look at how these types of issues have affected other companies in your industry before writing about them. Its enough just to say theyre a problem without showing evidence.
- What specific security measures are taken now for your current network?
- What other non-security factors should be considered with security management?
5. Power Supply Management
Its also important to consider environmental issues when designing an IT infrastructure so look at the data center operations section below. Youll want to talk about power consumption and how it pertains to your company or organization specifically.
6. Data Center Operations
7. Environmental concerns
What other non-environmental factors should be considered when designing an IT infrastructure for a data center?