Creating An Active Directory And Dns Domain On Windows
This task creates the domain wmq.example.com on aWindows 2008 domain controller calledsun. It configures the Domain mqm globalgroup in the domain, with the correct rights, and with one user.
In a production scale configuration, you might have to tailor the configuration to anexisting domain. For example, you might define different domain groups to authorize differentshares, and to group the user IDs that run queue managers.
- sun
- A Windows Server 2008 domain controller. It owns the wmq.example.com domain that contains Sun, mars, and venus. For the purposes of illustration, it is also used as the file server.
- A Windows Server 2008 used as the first IBM® MQ server. It contains one instance of the multi-instancequeue manager called QMGR.
- venus
- A Windows Server 2008 used as the second IBM MQ server. It contains the second instance of themulti-instance queue manager called QMGR.
Replace the italicized names in the example, with names of your choosing.
Configuring Secure Ldaps On Domain Controller
After installing and configuring Certification Authority server, Next step is use it to generate SSL certificate for LDAPS configuration on Domain Controller.
The Lightweight Directory Access Protocol is used to read from and write to Active Directory. By default, LDAP traffic is transmitted unsecured. You can make LDAP traffic confidential and secure by using Secure Sockets Layer / Transport Layer Security technology. You can enable LDAP over SSL by installing a properly formatted certificate from either a Microsoft certification authority or a non-Microsoft CA according to the guidelines in this article.
This will help to install certificates, which are digital credentials used to connect to wireless networks, protect content, establish identity, and do other security-related tasks.
To enable LDAPS, you must install a certificate that meets the following requirements:
- A private key that matches the certificate is present in the Local Computer’s store and is correctly associated with the certificate. The private key must not have strong private key protection enabled.
- The LDAPS certificate is located in the Local Computer’s Personal certificate store .
- The Active Directory fully qualified domain name of the domain controller must appear in one of the following places:
- DNS entry in the Subject Alternative Name extension.
- The Common Name in the Subject field.
Useful Articles
Active Directory Sites & Services
Its important to create a new site with a corresponding subnet that whill contain your new domain controller. Clients will try to contact the domain controller in their subnet first so a misconfiguration can cause slow logons or other problems. If your on-premises subnet isnt visible here you should create this one too!
Read Also: Transfer Wix To Shopify
Add A Windows Server 2022 Active Directory Domain Controller To An Existing Domain
For the installation of the AD DS role, I let you reread the beginning of the tutorial.
Before launching the Active Directory services configuration wizard, we will make sure that the server resolves the domain.
From a command prompt, ping the domain.
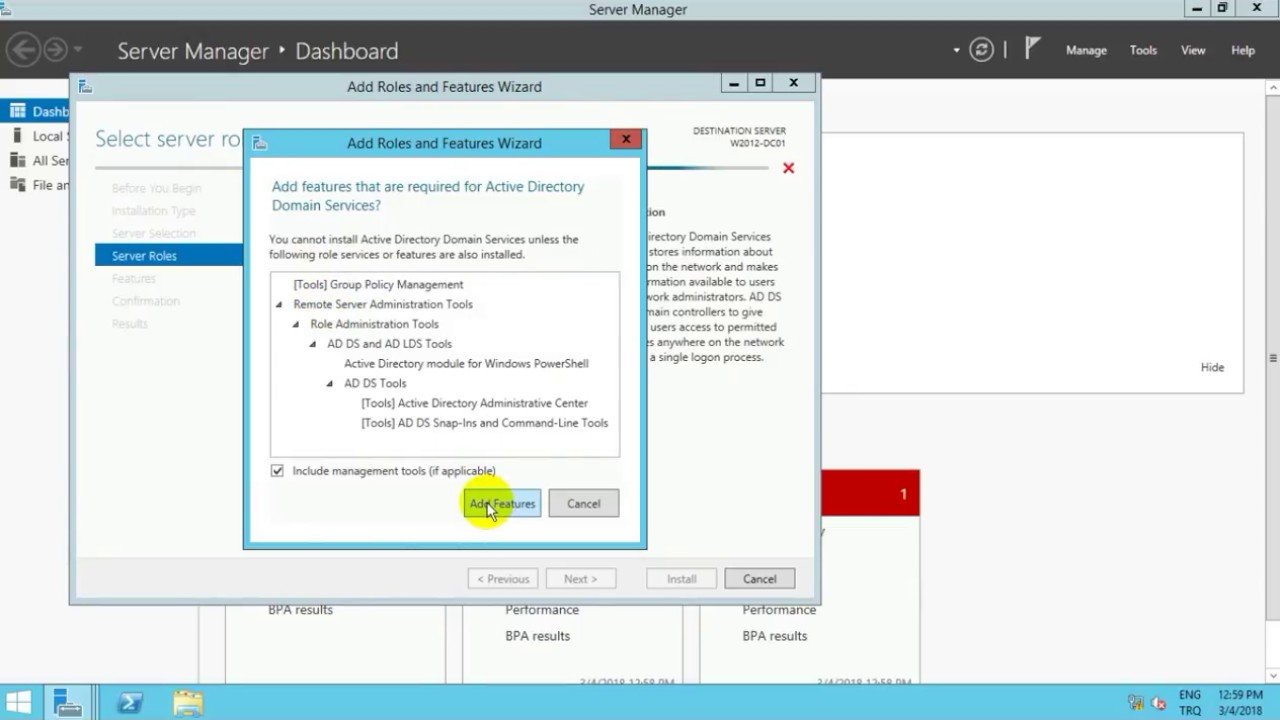
From the notification area, start the wizard by clicking on Promote this server to a domain controller 1.
When the wizard is launched, let select: Add a domain controller to an existing domain 1 and click on the Modify button 2 to indicate an account that is a member of the Domain Admins group.
Enter the username 1 then the password 2 and click OK 3.
Reminder: in the event of a schema version upgrade , the account indicated must be a member of the Company Administrators and Schema Administrators group. Once the operation is complete, the account will need to be removed from the groups.
If the information is correct, the domain is automatically added 1, click on Next 2.
If the domain is not added, click on the Select button to choose it.
In the Domain controller options part, check the box DNS server 1 then enter the DSRM password 2 and click Next 3.
Check that the Global Catalog box is checked. In a single-domain environment, the recommendation is to leave all domain controllers with the Global Catalog option.
In the DNS options, uncheck the Update DNS delegation 1 box and click Next 2.
Skip the installation options by clicking Next 1.
If necessary, change the default folders, otherwise click on Next 1.
Configure Your Ad Domain Controller Options
Post-deployment , we can now start to configure our Active Directory Domain Services and DNS settings.
Select “Add a new forest”, and specify the domain information for this operation that you would like here. You can put anything you would like here.
In my example, I have set this root domain name as: vulongtran.com.
You can put something like cars.local, pets.locals or any other domain you would like here as we are just testing this so having a domain name here at this stage will be useful. We can change this later on if needed.
Set a Directory Services Restore Mode password. You can choose any DSRM password you would like here.
It is important to keep note of this, as the Directory Services Restore Mode is a safe mode boot option for Windows Server domain controllers. DSRM allows an administrator to repair or recover to repair or restore an Active Directory database.
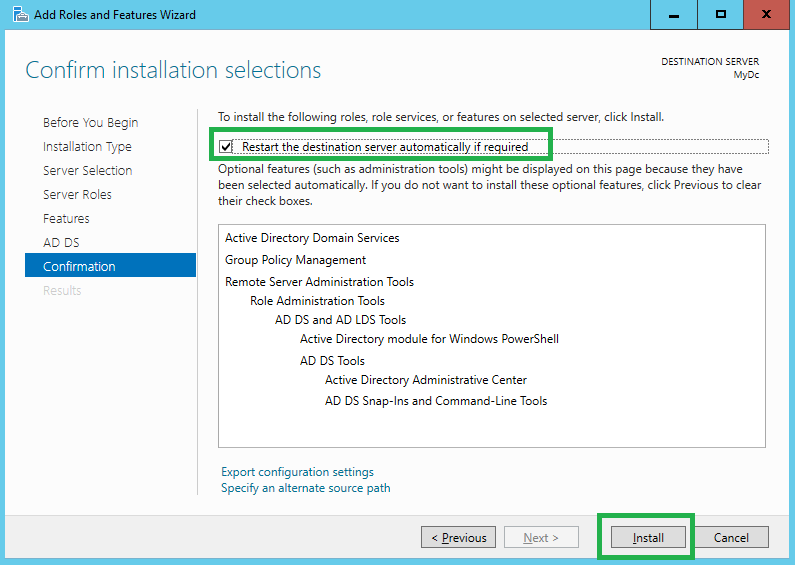
Follow the prompts and select the defaults and click “Next” accordingly.
When you are ready, click “install”.
Wait for the items to be installed. It may take 10-15 minutes or more.
You will be prompted to restart your computer when it is ready.
“You’re about to be signed out. The computer is being restarted because Active Directory Domain Services was installed or removed.”
Read Also: Register Domain Privately
About The Active Directory Time Hierarchy
In every Active Directory environment, time is synchronized in a hierarchy. This hierarchy is depicted in the below image, courtesy of the Time Synchronization in Active Directory Forests page in the Microsoft TechNet Wiki:
The Domain Controller holding the Primary Domain Controller emulator Flexible Single Master Operations role in the root domain represents the top of the hierarchy and is considered the authoritative time source. Thats why the Active Directory Best Practices Analyzer reports an action when this Domain Controller does not synchronize its time with an external source, like a pool of NTP servers on the Internet or a couple of GPS-equipped internal appliances, or a combination of both.
The Domain Controller holding the PDCe FSMO role represents the top. It is important to identify the Domain Controller with the PDCe FSMO role, as we need to perform changes on this host.
To Configure Windows Active Directory Anddomain Controller
Log in as an administrator to the Windows 2000 or 2003server host.
From the Start menu, go to Administrative Tools > ManageYour Server.
On the Manage Your Server wizard, choose Adding Rolesto Your Sever.
In the Server Role window, choose Domain Controller .
Accept the default values by clicking Next.
Continue to accept the default values and clicking Nextuntil the Report DNS Issue window is displayed.
This window is displayed when no properly configured DNSexists for Active Directory. Choose Install and Configure DNSto proceed to the next window.
Continue to accept the default values and clicking Nextuntil the Summary window is displayed, then click Next.
TheActive Directory Installation wizard is invoked.
Install the Active Directory Domain Controller.
Fordetailed instructions, see Install Active Directory Domain Services onthe Windows Server 2008-Based Member Server
Install Windows Support Tools.
Windows SupportTools contains the ktpass Kerberos tool you needto map a service principal with an Active Directory account. For informationabout ktpass, see the
Create a new user account.
From the Start menu, go to Programs > Administration Tools.
Choose Active Directory Users and Computers.
Enter a user name and password for the new user, and createthe user.
Create a user account to map to the Kerberos service.
From the Start menu, go to Programs > Administration Tools.
Choose Active Directory Users and Computers.
Don’t Miss: How Much Do Domains Cost Per Year
Synchronizing Active Directory User Accounts
Synchronizing Active Directory user accounts allows you to retrieve information about the user associated with a particular event, such as the user name, the userâs email address, and the userâs contact details. The user information comes from the Active Directory server in your environment. You can also view all the userâs recent activities.
Using the Change Guardian web console, you add one or more user containers and the user attributes that you want to synchronize.
To view and manage synchronized Active Directory accounts:
In the Change Guardian web console, click Integration.
Managing Remote Offices With A Universal Ad Extension
Over the last few years, a modern cloud solution has emerged that lets you securely extend Active Directory identities from your home DC to any remote location without any additional networking or hardware. Layered on top of AD, this solution can act as a two-way identity bridge between remote workstations and the home DC, securely writing user credential changes back to the AD database.
This AD integration is designed to be OS-agnostic, allowing Mac® and Linux® systems in any location to integrate with your on-prem directory. It even extends remote system management capabilities to these machines, with the ability to push GPO-like functions to all three major operating systems.
For those organizations that are shifting to a more remote workforce and eliminating remote offices, a cloud identity bridge can be a powerful concept, but even thinking about shifting your directory to the cloud may offer more advantages. IT organizations can completely manage and control access to a wide range of IT resources including systems, applications, files, and networks regardless of platform, protocol, provider, and location. That gives IT a massive amount of flexibility to react to the changing needs of the business whether expanding or contracting remote offices is the right decision. It will also help shape a decision as to whether shifting to a completely remote workforce is the right answer for the organization.
Recommended Reading: Migrate Wix To Shopify
How To Setup Active Directory
To begin you will need to first make sure that you have Windows Professional or Windows Enterprise installed otherwise you wont be able to install Remote Server Administration Tools. Then do the following:
For Windows 10 Version 1809:
For Windows 8
Create A New Active Directory Domain By Promoting The First Domain Controller
In this part, we will see how to create an Active Directory environment with the promotion of the first domain controller.
In production, it is recommended to have at least 2 domain controllers.
From the server manager, click on the notification icon then on Promote this server to a domain controller 2 to start the wizard.
The promotion wizard starts, before Windows Server 2012, we used the dcpromo.exe command
Select the operation: Add a new forest 1 then enter the domain root name 2 and click on Next 3.
The root name must be composed of a tld public or not and a name which can be that of your company for example.
The domain does not have to be registered.
For practical reasons, we avoid using a public domain that we use, such as that of the companys Internet site.
Also take into account, that this name will be used for user logon in the form
If you want users to open their session with their email address, it is possible to add a UPN suffix later, which allows you to have
Enter a password for Directory Services Restore Mode 1 and click Next 2.
The DSRM password must imperatively be noted somewhere, it allows you to connect to the server if the AD DS services no longer work and to allow a repair.
The DNS server role is installed on the domain controller, which is normal, a lot of Active Directory services rely on DNS records, which allows the client to find domain controllers.
On the screenshot, we can see that the functional level is Windows Server 2016.
Recommended Reading: Can I Transfer My Wix Website To Shopify
To Allow Corp2 Computers To Automatically Obtain Computer Certificates
On APP1, click Start, type certtmpl.msc, and then press ENTER.
In the Certificates Template Console, in the middle pane, double-click Client-Server Authentication.
On the Client-Server Authentication Properties dialog box, click the Security tab.
Click Add, and on the Select Users, Computers, Service Accounts, or Groups dialog box, click Locations.
On the Locations dialog box, in Location, expand corp.contoso.com, click corp2.corp.contoso.com, and then click OK.
In Enter the object names to select, type Domain Admins Domain Computers and then click OK.
On the Client-Server Authentication Properties dialog box, in Group or user names, click Domain Admins , and in Permissions for Domain Admins, in the Allow column, select Write and Enroll.
In Group or user names, click Domain Computers , and in Permissions for Domain Computers, in the Allow column, select Enroll and Autoenroll, and then click OK.
Close the Certificate Templates Console.
Primary: Get The Ip Address Of The Primary Active Directory Domain Controller
Login to your Primary Active Directory Windows Server.
Right-click on the Window Icon on the bottom-left of the screen. Then click Command Prompt.
On the command prompt window type ipconfig then Enter.
Note the IPv4 Address. You will need this later on the Secondary Windows Server.
In my case the IPv4 Address is 172.31.25.216. Yours would be different since you have a different network.
Once you have the IPv4 you may log out of the Primary AD Windows Server.
Also Check: Transferring Domain From Wix To Shopify
Secondary: Check Active Directory Users And Computers
Click on the Window-Icon on the bottom-left and then click Server Manager.
Click on Toolsand click on Active Directory Users and Computers from the list.
The Active Directory Users and Computers window will appear.
Double-click on the domain on the sidebar to expand the folder tree. Then click on Domain Controllers.
As you can see from the above photo that we now have 2 Domain Controllers. The Primary and Secondary Windows Servers.
Click on the Window-Icon on the bottom-left and then click Server Manager.
Click on Tools, then DNS.
On the DNS Manager window, double-click on the Computer Name . Then double-click on Forward Lookup Zones, then click on your domain .
You will see on the records that your Primary and Secondary AD Windows Server are listed as Name Servers so they are now responsible for being the DNS Servers on your network.
We have now successfuly setup and checked our Secondary Active Directory Windows Server.
If anything happens with our Primary Server, the Secondary Server will be our back-up.
If you have any questions, comments or corrections on the above steps let me know on the comments below. I would still like to learn more about Windows Active Directory.