Woman Jumps In Front Of Train Today
24) What do you understand by domain trees and forests? Domain trees and forests both are two important concepts of Active Directory. A domain tree is a collection of one or more domains that share a common namespace. For example, jobs.career.com and career.com both domains are a part of the career.com domain tree. Domain Controllers rely on SRV records registered in the DNS Server to perform important functions such as replicating changes and allow Active Directory clients to locate domain controller services. Any application that uses SRV records to find a domain controller will fail if SRV records for domain controllers are not registered. Active Directory domain services Hierarchical structure explained. Alright so lets talk a bit about Active Directorys hierarchical structure. Essentially, the hierarchical structure of an AD is comprised of forests, trees, domains, and organizational units .
Other Domain Controller Implementation Options
The following options are available when setting up a domain controller with AD:
- Domain Name System server: The domain controller can be configured to function as a DNS server. Dell recommends configuring at least one domain controller as a DNS server.
- Global Catalog capabilities: The domain controller can be configured to use Global Catalog, which enables the controller to return AD information about any object in the organization, regardless of whether the object is in the same domain as the domain controller. This is useful for large enterprises with multiple AD domains.
- Read only domain controller : Domain controllers used in branch offices or in other circumstances where network connectivity is limited can be configured as read-only.
- Directory Services Restore Mode : DSRM provides the option to do emergency maintenance, including restoring backups, on the domain controller. A DSRM password must be configured in advance.
Chapter 12 Managing Domain Controllers
Domain controllers are the most essential part of your Active Directory. Creating domain controllers was covered in detail in chapter 11, and this chapter shows how to manage them. It starts with discovering the domain controllers in your environment, and then covers testing their availability and the services they offer.
The chapter then moves on to global catalogsthe extra piece of domain controller functionality that enables you to access a subset of the attributes of every object in the forest in every domain. The global catalog is essential for the correct functioning of a multi-domain forest and Exchange email servers. After learning how to find global catalogs, youll see techniques for promoting domain controllers to be global catalogs .
In Active Directory all domain controllers are equal, but some roles can only be performed by one domain controller at a time. These are the Flexible Single Master Operations roles. You need to know how to discover the FSMO role holders, what they do, and how to move the role between domain controllers. The chapter also includes a lab section.
First uphow to discover the domain controllers in your environment.
Don’t Miss: Io Domain Name Meaning
What Is The Main Use Of Domain Controller:
The DC’s primary responsibility is to authenticate and confirm network user access.
When users log into their domain, the DC examines their login, password, and other credentials to determine if they should be granted or denied access.
The most common examples are Microsoft Active Directory or Microsoft Azure AD, whereas Samba is the Linux-based counterpart DC.
What Is The Role Of Active Directory
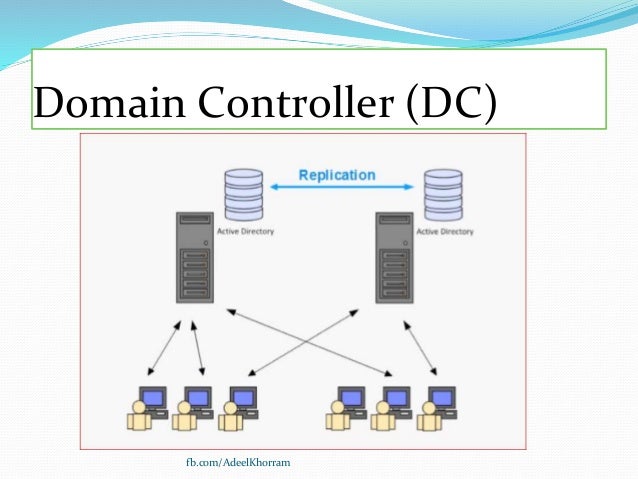
Since Active Directory is mentioned a lot, and I will keep mentioning it, its time to explain what it is. Essentially, its the central database that stores everything about a company. I dont mean that it stores files and images, but it stores the users, clients, and servers.
Lets put this in a story for easier understanding. Take, Sara. She starts a new job at Company A. If Sara is ever going to be able to login to the computers, she needs to have an active account in Active Directory. This is because when Sara tries to log in to a computer, the computer will check with Active Directory to see if Sara exist as a user and if she is permitted to log in to the computer.
When Sara has logged in, she needs to print out some documents. Because she is part of Active Directory, as well as the computer she is on, she can easily reach a shared network drive where the document is. Because Active Directory also has sent out some default settings for her, she already has the office printer installed and set as default printer, making it easier for Sara to print out the document.
Active Directory holds all the users, computers and servers. But its important to note that what holds everything together is a domain, not Active Directory. The AD should be seen as a database that holds information while a domain is what makes everything talk to each other.
Read Also: How Much Does It Cost To Own A Domain
Active Directory Trust Relationships And Types
A trust relationship is the formation of a logical link between two domains. One of them is known as the trusting domain, and the other is called the trusted domain. With a trust relationship, the trusting domain will honor the login authentication of the trusted domain.
Usually, the trusted domain stores the users, while the trusting domain comprises network resources. Thus, the users in the trusted domain are trusted and are allowed to access resources stored in the trusting domain.
Trusts can be created manually or automatically. These trusts are further classified into two categories viztransitive and non-transitive trust. Transitive trust simply implies that if Domain 1 trusts Domain 2 and Domain 2 trusts Domain 3, then Domain 1 trusts Domain 3 as well. Non-transitive trust means that if Domain 1 trusts Domain 2, and Domain 2 trusts Domain 3, then Domain 1 DOES NOT trust Domain 3.
Trusts can further be one-way or two-way. Following are the types of trust relationships that are either one-way or two-way by default:
Can I Have Multiple Servers Running Active Directory Domain Services
Yes! In fact, thats the norm: Organizations almost always have multiple domain controllers for redundancy and scalability. If one DC fails, another one can step in to provide the same services.
The Active Directory replication service makes sure that all the domain controllers on the network stay in sync. In particular, it keeps them all up to date on any modifications to the users and computers in your directory , and any changes to your schema, which defines all the object classes that can be stored in your directory.
Don’t Miss: Connect Godaddy To Shopify
What Is Active Directory
Active Directory is a directory service developed by Microsoft. It has information about the users, computers, resources such as files and folders and printers. Usually, it operates like a telephone directory. Therefore, it arranges the users and resources into groupings. Windows Server operating system consists of Active Directory as a set of processes and services. Furthermore, it uses the Lightweight Directory Access Protocol version 2 and 3, Microsoft version of Kerberos and DNS.
The Active Directory Services consist of multiple directory services, which are called Active Directory Domain Services.
Dynamic Host Configuration Protocol
The DHCP is a network management protocol used for dynamic address allocation. The protocol relies on the DHCP server to automatically provision IP addresses, default gateway, and other information to DHCP clients. Active Directory depends on a DHCP server to start responding to client requests.
When a client using DHCP connects to a network, it instantly sends a DHCP discovery to find the server, which in turn sends a DHCP offer with an available IP address.
You May Like: Shopify Transfer Domain
S To Adding Your Windows 10 Computer To The Active Directory:
Be sure you are connected to the LBNL network: LBNL wired network, lbnl-employee WiFi, LBNL VPN
What Are The Best Practices For Protecting Domain Controllers
Glad you asked! Its essential to remember that any server running AD DS is a top target for cyberattacks. A hacker who compromises one of your domain controllers is well-positioned to achieve whatever nefarious goals they have, from stealing your most valuable data to sabotaging critical business processes. And, as Microsoft points out, Depending on an attackers preparation, tooling, and skill, modification or even irreparable damage to the AD DS database can be completed in minutes to hours, not days or weeks.
Therefore, its essential to protect your domain controllers like Fort Knox. In particular:
Also Check: Transfer Godaddy Domain To Wix
Active Directory Reporting With Solarwinds Access Rights Manager
Generating reports on Active Directory is essential for optimizing performance and staying in accordance with regulatory compliance. One of the best Active Directory reporting tools is SolarWinds Access Rights Manager . The tool has been created to increase visibility into how directory credentials are used and managed. For example, you can view accounts with insecure configurations and credential abuse that could indicate a cyber attack.
Using a third-party tool like SolarWinds Access Rights Manager is beneficial because it provides you with information and features that would be much more difficult or impossible to access through Active Directory directly.
As well as generating reports you can automatically delete inactive or expired accounts that cybercriminals target. SolarWinds Access Rights Manager starts at $3,444 . There is also a 30-day free trial version that you can download.
See also:Access Rights Management
How Do I Install Active Directory Domain Services
You dont install AD DS per se. Rather, it is one of the server roles included in the Microsoft Windows Server operating system. When you install Windows Server on a machine, you need to specify what role or roles that server will play: file server, web server, DNS server and so on .
Figure 1. When you install Windows Server on a machine, you need to specify what roles that server will play.
As you can see in the figure, there are a variety of other roles you can assign to a server, including:
- Active Directory Certificate Services Enables the DC to serve digital certificates, signatures and public key cryptography
- Active Directory Federation Services Provides single sign-on so users dont have to keep providing the same credentials
- Active Directory Lightweight Directory Services Enables use of LDAP for communicating with other directory services servers, such as any Linux computers in your network
- Active Directory Rights Management Services Helps protect information through persistent usage policies that remain with the content no matter where it is moved
Don’t Miss: How Much Do Domain Names Cost
What Is A Primary Domain Controller
A best practice for all companies that use Active Directory, is to have at least two domain controllers. This is for redundancy so that if one goes down, the company can keep working while IT freaks out. Preferably, the domain controllers should be at different places physically.
Another benefit of having multiple DCs could be that you have them in different locations. Say if the company has an office in Country A and another in Country B. Instead of having users in Country B to connect to A, the authentication process can be sped up if there is a DC in the office for Country B. So, having a DC in each country can be a good idea.
Over to primary domain controllers. A Primary Domain Controller was a DC that was number one, so to speak. There were always one primary DC and the other one were backup DCs. In 2008, Microsoft changed this so if you have a domain controller from 2008 or later, the concept of primary and backup domain controllers has disappeared.
All domain controllers are now being treated equally. Active Directory is synced to all of these machines and anyone can be used for anything since they are working the same way. However, you might keep hearing about PDC and BDC because many IT guys are used to it.
Active Directory Federation Services
The Active Directory Federation Service is an identity management services solution.
It provides Single-Sign-On access control for web applications, web sites, or multiple resources within a network.
The AD FS gives flexibility when accessing multiple resources. End-users only need to remember a set of credentials to use them all across these resources.
When a user signs in to a workstation, the authentication claim can be used by third-party applications on behalf of AD.
AD FS sends the authentication claim rather than credentials.
Don’t Miss: Transfer Shopify Domain To Godaddy
Create Dedicated Workstation Hosts Without Internet And Email Access
Administrators need to manage job responsibilities that require sensitive administrator rights from a dedicated workstation because they do not have easy physical access to the servers. A workstation that is connected to the Internet and has email and web browsing access is regularly exposed to compromise through phishing, downloading, and other types of Internet attacks. Because of these threats, it is a best practice to set these administrators up by using workstations that are dedicated to administrative duties only, and not provide access to the Internet, including email and web browsing. For more information, see .
Note
If the administrators in your environment can sign in locally to managed servers and perform all tasks without elevated rights or domain rights from their workstation, you can skip this task.
-
Minimum. Build dedicated administrative workstations and block Internet access on those workstations including web browsing and email. Use the following ways to block Internet access:
-
Configure authenticating boundary proxy services, if they are deployed, to disallow administrator accounts from accessing the Internet.
-
Configure boundary firewall or proxy services to disallow Internet access for the IP addresses that are assigned to dedicated administrative workstations.
-
Block outbound access to the boundary proxy servers in the Windows Firewall.
The instructions for meeting this minimum requirement are described in the following procedure.
Note