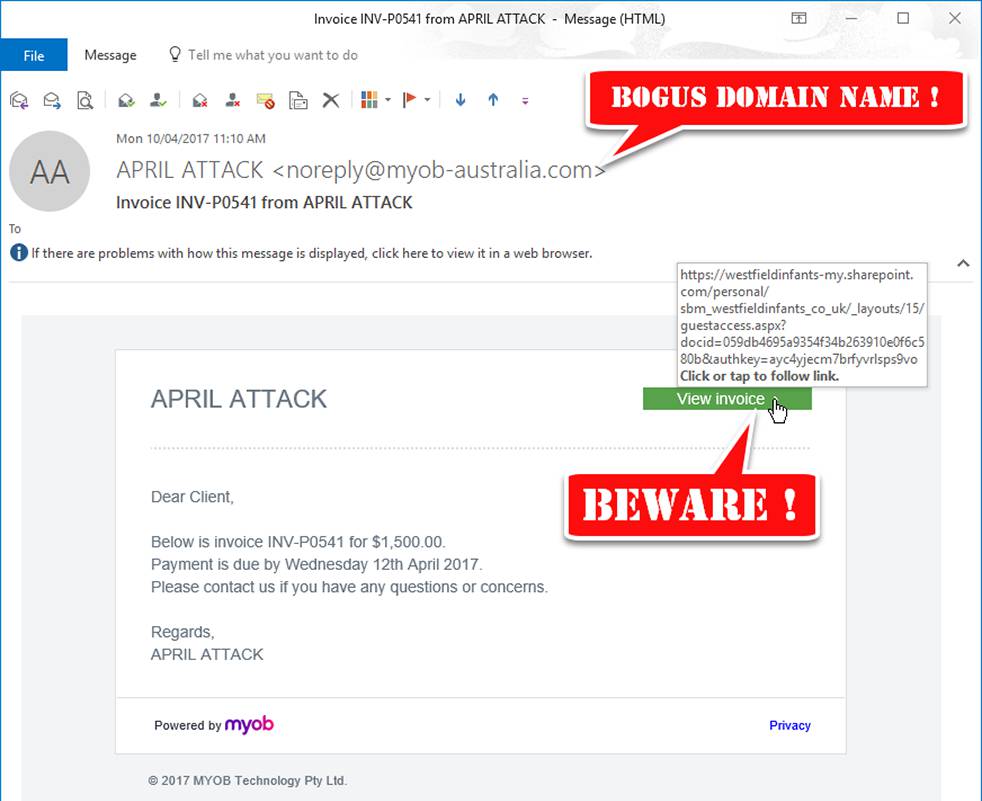
Why Do Scammers Spoof Your Address
Scammers send you emails that appear to come from your address for one of two reasons, generally. The first is in the hopes they will bypass your spam protection. If you send yourself an email, youre likely trying to remember something important and wouldnt want that message labeled as Spam. So, scammers hope that by using your address, your spam filters wont notice, and their message will go through. Tools do exist to identify an email sent from a domain other than the one it claims to be from, but your email provider must implement themand, unfortunately, many dont.
The second reason scammers spoof your email address is to gain a sense of legitimacy. Its not uncommon for a spoofed email to claim your account is compromised. That you sent yourself this email serves as proof of the hackers access. They might also include a password or phone number pulled from a breached database as further proof.
The scammer usually then claims to have compromising information about you or pictures taken from your webcam. He then threatens to release the data to your closest contacts unless you pay a ransom. It sounds believable at first after all, they seem to have access to your email account. But thats the pointthe scam artist is faking evidence.
RELATED:What is Typosquatting and How Do Scammers Use it?
What Actions Can You Take To Prevent Spoofing Attacks
You can’t stop hackers from sending spoofed messages, but you can learn various tips to identify and prevent email spoofing:
- Educate employees via conducting awareness training and mock phishing scenarios. You can teach them about the key characteristics of phished and spoof emails.
- Make sure to keep your anti-virus and anti-spyware software and your firewall updated.
- Be careful while opening or downloading email attachments, even if they appear from a known source.
- Improve your email security by deploying spam filters for detecting viruses, blank senders, etc.
- Try not to send sensitive data via email.
- Encrypt your and your organization’s sensitive and personal information.
- Look out for URL redirects and pay attention to subtle differences in the website content.
Also read – How To Detect Phishing Emails And Safeguard Against Them.
How To Protect Your Customers From Domain Name Spoofing
The best way to protect your customers from domain name spoofing is by sending cryptographically signed emails from an authenticated email server. That way when they receive your message theyll know it came from you and it hasnt been tampered with.
There are two technologies you can deploy to combat domain name spoofing. The first is SPF, or Sender Policy Framework. SPF prevents email spoofing by enabling the recipient to verify that the incoming emails IP address comes from a list of IP addresses authorized by the sender.
The other technology to prevent spoofing is DKIM . Email servers are configured to attach a cryptographic signature to the outgoing email. The attached signature has everything the receiving party needs to verify that the email came from the server it said it came from. Combined with DMARC and its reporting tools helps prevent phishing both inbound and outbound phishing with your domain.
Don’t Miss: How To Find Out Who Owns Domains
How To Turn Off Email For Parked Domains
It might seem counterintuitive: Why publish a DomainKeys Identified Mail record in your DNS if you’re never going to cryptographically sign outgoing email? Why publish a Sender Policy Framework record if there will never be genuine email coming from your domain? It’s a hack, that’s why. We’ve been trying to back-port security onto email for 40 years and still can’t get it quite right.
Combined with a DMARC record and a null mail exchanger record, these are the best practices for preventing spoofed mail being sent by a fraudster using a domain you own. Want to go deeper? The authoritative guide to securing email for parked domains can be found in this anti-spam working group document, the Messaging Malware Mobile Anti-Abuse Working Group from December, 2015, entitled “M3AAWG Protecting Parked Domains Best Common Practices”. If you need a primer on DMARC, DKIM and SPF, check out this CSO article.
Email Spoofing Protection: Spf Dkim And Dmarc
There are different solutions and ways to block attacks that use spoofed emails. Many vendors are investing in artificial intelligence and machine learning, which detect more sophisticated cases. Actually, this is our case here at Gatefy. But today I would like to stick to the three more common authentication mechanisms. They are powerful and simple tools that can help you fight email spoofing.
Theyre SPF , DKIM and DMARC . To be more specific, theyre mechanisms that identify the servers allowed to send emails using your domain. Besides, they have everything to do with our tips to improve your domain protection and prevent email spoofing.
Don’t Miss: What To Do After Buying A Domain Name
Can Your Email Domain Be Spoofed Check Your Domain Now
Do you know how secure your domain is? Most organizations operate with the assumption that their domains are highly secure and in a short while, they learn it isnt the case. One of the tell-tale signs of a low security score is if your domain name is being spoofed this means that someone is using your domain in order to impersonate you and fool email recipients. But why should you care? Because these spoofing activities can potentially endanger your reputation.
In a world full of domain impersonators, email domain spoofing shouldnt be something that companies take lightly. Those who do could be putting themselves, as well as their clients at risk. A domains security rating can have a huge effect on whether or not you get targeted by phishers looking to make a quick buck or to use your domain and brand to spread ransomware without you being aware!
Check your domains security rating with our Free DMARC Lookup tool. You may be surprised by what you learn!
Another Way To Detect Spoofed Emails
Various email authentication protocols have been developed to safeguard against email spoofing. These protocols ensure that email addresses, and email content is not tampered with. If emails have failed any of them, then the chances are that email is spoofed. You can check the pass/fail status by checking the original source of the email.
Lets discuss how each of these works:
Recommended Reading: How Much Do Domain Names Cost
Reasons For Email Spoofing
The reasons for email spoofing are quite straightforward. Usually, the criminal has something malicious in mind, like stealing the private data of a company. Here are the most common reasons behind this malicious activity:
- Phishing. Almost universally, email spoofing is a gateway for phishing. Pretending to be someone the recipient knows is a tactic to get the person to click on malicious links or provide sensitive information.
- Identity theft. Pretending to be someone else can help a criminal gather more data on the victim .
- Avoiding spam filters. Frequent switching between email addresses can help spammers avoid being blacklisted.
- Anonymity. Sometimes, a fake email address is used to simply hide the senders true identity.
The Spf Protocol: Securing The Sending Servers
The first step is to declare the servers. The SPF standard is a DNS record that defines the mail servers authorised to send messages for your domain. This protocol allows listing the servers and IP addresses authorised to use the domain name. This is the first step to authenticate your emails.
In fact, when a message from your organisation is sent, the recipients mail servers check that the mail comes from one of the authorised domains. If it doesnt come from an authorised domain, the message will arrive in spam.
Misconfigured SPF records can cause delivery problems. Depending on the email solution provider you use, they usually provide guidelines for configuration. You can also consult these best practices when configuring SPF.
Read Also: Can I Transfer My Wix Website To Shopify
Spoofing Via Lookalike Domains
Suppose a domain is protected, and domain spoofing isnt possible. In that case, the attacker is most likely going to set up a lookalike domain. In this type of attack, the fraudster registers and uses a domain that is similar to the impersonated domain, e.g.@doma1n.co instead of@domain.co. This change could be minimal enough not to be noticed by an inattentive reader. Its effective because when exactly was the last time you bothered to read an email header?
Using a very similar domain, which also bypasses spam checks due to being a legitimate mailbox, the attacker creates a sense of authority. It might be just enough to convince its victim to reveal their password, transfer money, or send some files. In all cases, email metadata investigation is the only way to confirm whether the message is genuine. However, its sometimes plain impossible to do on the go, especially with smaller smartphone screens.
What Are The Impacts Of Email Spoofing On Organizations
Email spoofing can cause a significant financial burden on an organization. The 2021 Cost of Phishing Study conducted by Polemon institute revealed that phishing cost has tripled since 2015, increasing from $3.8 million in 2015 to $14.8 million in 2021.
The phishing cost includes additional costs which can damage and hinder the growth of your organization. Some of the significant phishing costs are as follows:
- as they spend more time dealing with the consequences of phishing scams. Employee productivity losses become costlier to the organization, increasing from $1.8 million in 2015 to $3.2 million in 2021.
- Organizations are encountering an average of 5.3 compromises in their credentials over the past 12-month period.
- The average total cost of credential compromise not contained is $2.1 million and has increased significantly from $1 million in 2015.
- The cost of resolving malware infections has doubled the total cost of phishing. In addition, the costs due to non-containment of malware almost doubled from an average of $3.1 million in 2015 to $5.3 million in 2016.
- The average cost ofBusiness Email Compromise exploits was $5.96 million in 2021. BEC happens when the attacker targets employees who have access to an organization’s funds or data.
- Ransomware is a sophisticated malware that blocks victims’ access to their files. The average total cost of ransomware in 2021 was $5.66 million, with an average attack rate of 17.6%.
Recommended Reading: How To Transfer Godaddy Domain To Shopify
How Do You Send An Email
What a great question! To understand all of this article, we first need to understand how sending and recieving emails work. Sending and recieving emails is a fairly simple process, if you log into your corporate outlook email and press the compose button, add a recipient, subject and body and fire it off, it will be shot out to your companies email server on port 25 or 587. These ports are known as SMTP, or Simple Mail Transport Protocol. The whole entire purpose of SMTP is to just send emails.
Note: If youre using Port 25, youre automatically doing a bad. Port 25 is unencrypted and the contents of your email as well as your username and password are all in clear text! Oh no! So just use port 587. Its not that much more difficult to use. Always make sure youre usiong encrypted protocols or else bad things can and will happen. You have been warned.
Great, so now we know about SMTP, what does sending an email on the procotol level look like? Well, its actually suprisingly simple. Wikipedia was kind enough to outline a simple conversation with a Postfix SMTP server, heres the conversation:
Source: Simple Mail Transport Protocol via Wikipedia
Now, lets break it down. The first thing to know is that you dont actually need any special tools to interface with a SMTP server all you need is Netcat or Telnet.
Heres an example from my Inbox doesnt the Date, From and To look familiar?
So, thats it thats pretty much how sending an email works.
How Does The Attacker Carry Out Email Spoofing
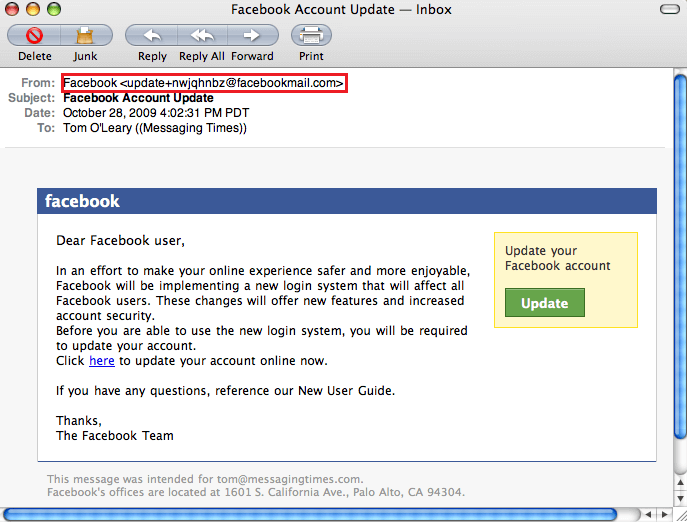
The attackers can carry out email spoofing with a working Simple Mail Transfer Protocol server.
- Once an email message is composed, the attacker can forge fields found within the message header, such as the From, Reply-to, and Return-path.
- When the user gets the email, it appears to come from a known source, while in reality, it had been sent by the attacker.
It is possible to forge these addresses because SMTP does not provide a way to authenticate addresses. Although protocols and methods have been developed to combat email spoofing, adoption of those methods has been slow.
Read Also: How To Figure Out Who Owns A Domain
What Is Email Impersonation Everything You Need To Know
- 16 March 2022
Tessian Cloud Email Security intelligently prevents advanced email threats and protects against data loss, to strengthen email security and build smarter security cultures in modern enterprises.
- What is email impersonation?
Email impersonation is a phishing technique. Cybercriminals create email addresses that look legitimate to trick their targets into trusting them.
Email impersonation might not be the most sophisticated phishing method, but its simple, its widespread, and it can be devastating. Heres why
The Danger Of Domain Spoofing
Domain spoofing is a type cyberattack where hackers use a fake or “spoofed” web domain or email address to impersonate an organization or one of its employees. Domain spoofing typically is conducted by sending emails or building websites with fake domain names that seem to be legitimate, but where the lettering of the domain address is changed in slight but in hard to detect ways. Spoofed websites or emails will mimic the organization’s design and branding to create an appearance of legitimacy. Users responding to email or web domain spoofing may be duped into revealing sensitive information, giving up their login credentials, wiring money to a fraudulent account or otherwise engaging in actions that harm the organization.
Mimecast provides easy-to-use, cloud-based solutions that effectively block domain spoofing and other web security threats in email and the web. With Mimecast Web Security and Mimecast Targeted Threat Protection, organizations get an integrated solution for protecting email and the web from domain spoofing and other email and web security threats.
Recommended Reading: Transfer Domain From Shopify To Wix
What Is The Definition Of Spoofing
Email spoofing is a technique used in spam and phishing attacks to trick users into thinking a message came from a person or entity they either know or can trust. In spoofing attacks, the sender forges email headers so that client software displays the fraudulent sender address, which most users take at face value. The email is meant to look exactly like something sent, in most cases, from a colleague, vendor or brand. The goal of cyber spoofing is to trick users into believing the email is legitimate so the recipient will divulge information, steal money, or take some other action.
There are many spoofing types including server spoofing.