Change Your Recovery Questions And Password Hints:
Along with the password, you should also change the password hints or recovery questions for your email address, since it is possible that someone guessed the answers in order to gain access to your email account. Make sure the questions are not related to information that could be found with a bit of sleuthing, such as birthdays, maiden names, place of birth, etc. For added security,consider typing a second password as your answer instead.
Learn How To Detect And Prevent Phishing Attacks
Phishing isnt a new technique, but its still an efficient one. Cybercriminals can use phishing attacks to withdraw money, steal your identity, open credit card accounts in your name, and further trade all that information about you, so be careful with what emails and attachments you open or what links you click on.
How To Hack Yahoo Email With Phishing Attack
Phishing Attack
Phishing Attack is a famous technique to hack any web-based password. This method is known for hacking Facebook and other social media site password.
But you can also hack Yahoo mail password with this approach. You can follow this process to complete this project successfully.
However, nowadays, almost all people know about phishing sites. You can still give a try if you have a single target.
Step 1:
At first, you will need a website to complete this process. So, set up a website first with suitable hosting. The domain should look like real.
Step 2:
Now collect the Yahoo phishing code from google and copy it. Then paste the codes on your website and save it. After that, your site will look exactly like the Yahoo login page.
Step 3:
Now send the site link to your victims. You will get the Yahoo mail password soon as they log in using your link.
Phishing is the most relevant way to hack someones Yahoo mail password. However, the process is illegal and also a cyber-crime. Almost all countries have strong laws against cyber-crime. So, we strongly discourage you from using it.
You can see some videos on
Recommended Reading: Should I Buy My Domain Through Shopify
Why Create A Edu Email
Edu email is one of the best email extension to which several Company provides offer and free services. These emails are provided only by colleges and universities or educational institutions to their students.
A .edu email not only assists you to get the information from the college administration, but it also serves as a means to get free access to the free services only available to students. Do you want to study abroad? Here is a guide on how to pick the school of your dreams.
Hence, lets discuss some offers and services provided to .edu emails.
How To Hack Yahoo Email With 4 Easy Steps
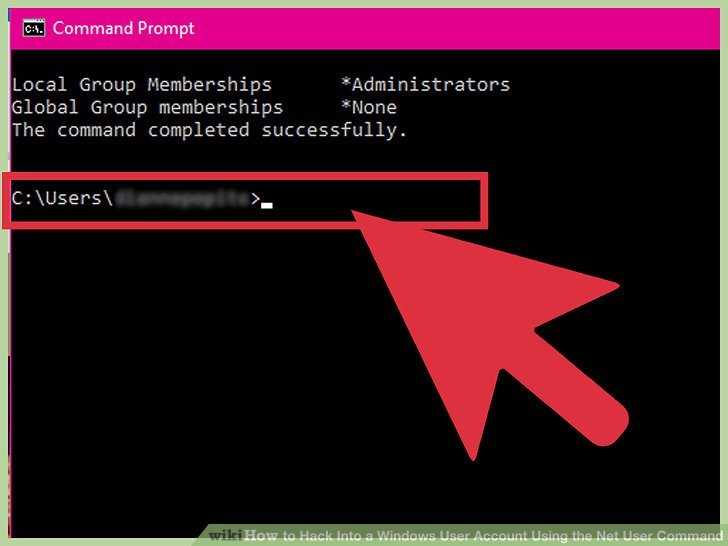
Do you ever wonder how to hack Yahoo email? A lot of people are searching for an answer. Yahoo is one of the most used operating systems of the current time along with Google. There are more than 280 million users on this email server.
Contents at a glance
Currently, Yahoo is the third-largest web-based email server in the world. However, they have leakage in their security system.
So you can use the leakage to get back your forgotten password easily. On the other hand, you can also use it for someones Yahoo account key hack.
In this article, we will show you how to use the leakage of the Yahoo mail server and hack anyones account. You can spy on anyones account without getting noticed. The process is pretty easy, and even non-IT background people can also do it.
However, we are firmly discouraged to hack someone else Yahoo email without any reason. Keep reading this article to know more about how to hack emails.
Don’t Miss: How Much Does It Cost To Buy A Domain
How To Protect Your Organization
This vulnerability may be resolved with a reconfiguration.
Reconfigure Office 365
You must block direct delivery, reconfigure inbound relaying, and close the vulnerability. Make sure that Office 365 only accepts emails from the gateway.
In his blog, Akers offers another solution. He recommends creating a new connector and transport rule so that emails follow the correct MX path.
Reconfigure Gmail
If you use Gmail, you must deactivate your users’ test addresses. To do so, remove the domain alias your_domain.com.test-google-a.com so that it no longer points directly to user mailboxes.
Topics Of Phishing Letters
Account problems
As regards the text of the letters, most of them begin by suggesting there is a problem with the victims e-mail account: storage limit reached, letter delivery problem, unauthorized login, spamming accusations, alerts of other violations, and so forth.
The letter normally tells the user how to deal with the problem mostly by confirming or updating account data by following a link or opening an attachment. To frighten the recipient, it says if they dont follow the instructions, the account will be blocked or deleted.
In almost every case, the letter sets a time frame for response, somewhere from several hours to several weeks. Usually, its 24 hours both credible and not long enough to let the victim relax and forget about the letter.
Your account will be deleted within 24 hours due to spamming. Threats and time limits are typical phishing tricks
Imitation of business correspondence
Sometimes, atypical phishing letters target e-mail accounts. The text of such messages may make no reference at all to e-mail or account data. The letter may look quite like real business correspondence.
We should mention that the volume of fake business letters used for phishing has grown in the past few years. Messages of this type are usually used to deliver harmful attachments, but some of them also phish for personal data. A regular user may have a hard time detecting a phishing letter cybercrime counts on that.
Recommended Reading: How Much For A Domain Name Per Year
Phishing Letters The Most Common E
The vast majority of scam letters made to steal e-mail login names and passwords look like messages originating from the services we use for e-mail. When targeting home users, phishers mimic popular webmail services. And when attempting to hack corporate accounts, they pretend to be your work e-mail service in this case the sender is simply the mail server.
Popular mail services are imitated much more often. Scammers try to make such letters as convincing as possible. The deception toolkit is the standard one: a senders address that looks much like the real one, logos, headers and footers, links to official resources, a plausible layout, etc.
Phishing letter frightening user with account deletion
As for the corporate accounts, scammers often send phishing letters disguised as messages from corporate server or public e-mail services to shared addresses , but sometimes such letters reach the mailboxes of individual employees whose addresses have somehow ended up in spam databases.
Companies that want to be taken seriously, large ones in particular, maintain e-mail servers of their own. The logins and passwords for such accounts are also appealing to attackers. Their messages are often betrayed by less-than-perfect appearance sender addresses from free webmail services, spelling errors, etc. but even such letters may be taken by inexperienced employees for the real thing.
In this letter an exceeded quota alert is imitated by phishers
Setting Up For Success
You May Like: How To Switch From Godaddy To Shopify
What Are The Benefits Of Edu Email
Here are some of the benefits of having a .edu email.
1. GitHub Student Developer Pack
The first and biggest benefit of having a .EDUs email address is the GitHub Student Developer Pack, the best free developer tools, and services for students. This student pack comes with 12 great offers and free services that may be useful to you, such as $15 Amazon AWS coupon, $50 Digital Ocean coupon and much more.
If you are planning to apply to .edu for the GitHub student Pack benefit then stop here. You dont have to go through all the articles. Just read the FAQ Question number 2. We have it covered there.
Take a look at the list below:
2. Amazon Student Pack
When you use an .EDU email account and sign up for an you will be able to use this Edu email for Amazon Prime for free for six months, which has many benefits:
- Free TWO-DAY shipping on many Amazon products.
- Get unlimited instant streaming of movies, TV shows, and music.
- Access exclusive deals for students.
- Unlimited photo storage with Amazon Prime Photos.
3. LastPass
LastPass offers six months of the LastPass Premium for any users with a .EDU email address.
4. Newegg Premier
Grab one year of Newegg Premier that costs you $50. Just sign up for the Newegg Premier account with your student email account.
5. Apple
You will help yourself saving a lot of money by using the .EDU email address to purchase products from Apple. There are changes to save up to $200 on Apple computers.
6. Microsoft DreamSpark
Is It Possible To Hack Yahoo Mail
Everything is Possible
We already mentioned that there is some leakage in the Yahoo mails security. Nowadays, Yahoo mail password hacking is typical news we often heard in the newspapers.
You May Like These:
No products found.
Besides, recently Yahoo revealed that hackers hacked almost 32 million Yahoo passwords in the last two years. It was done by a simple method known as forged cookies. This incident proves the leakage of Yahoo email security.
Hackers use some password decrypting software to hack Yahoo email. But this is true that there is no readymade software for hacking Yahoo email password directly. However, phishing is the best way to hack Yahoo password.
Hackers create a login page that exactly looks like the Yahoo login page and sends the password to their server. On the other hand, there are some different working ways to hack Yahoo password.
Read Also: Transfer Shopify Domain To Another Host
Why Is This Happening
If you use Office 365 and G Suite, you have a root domain. The DNS of these root domains are managed by Google and Microsoft not by you.
If you use an email security gateway , you probably changed your MX records to point to the gateway so it can scan your emails. But you can’t change the MX records of root domains, because they aren’t managed by your organization. This means that you can’t point the MX record of your root domain to your gateway.
As a result, your email gateway doesn’t scan messages sent directly to the root domain. Hackers are taking advantage of this loophole to send phishing emails directly to end users.
How Can A Low Domain Security Impact Your Organization
As most organizations send and receive data through email, it is crucial that they use a secure connection in order to protect their brand. In the event of inadequate email security, it can lead to big problems for both enterprises and individuals. In terms of communication platforms, email is still the most widely used. Email sent out from a data breach or hack can be devastating for your organization’s reputation. Such spoofed emails can also facilitate the spread of malware, spyware, and spam. It is therefore imperative to re-examine how security is deployed within email platforms.
In 2020 alone, brand impersonation accounted for 81% of all phishing attacks, while a single spear-phishing attack resulted in an average loss of $1.6 million. Security researchers predict that this will double by the end of 2021. In turn, this increases the need for organizations to improve their email security as soon as possible.
In contrast to multinational businesses, small businesses and SMEs are still averse to the idea of implementing email security protocols. This is because it’s a common myth that SMEs do not fall on the potential target radar of cyber-attackers. Unfortunately, that isn’t true. Hackers target organizations based on the security vulnerabilities and problems of their email security, not on the size of the organization. Therefore, any organization with poor domain security might be a target.
Recommended Reading: How Much Are Domains
Github Student Developer Pack
You can demand a Github Student Developer Pack which will give you a variation of discounts and free stuff. This is the greatest benefit of an Edu email account, and you can receive $1000 and more value of free value using this pack.
It is very simple to sign up for a Student Developer Pack on Github using your .edu email account
- Just visit this link and click on the Get your pack button in the center.
- On the next page, you can demand a discount and fill up the signup form then, wait for 5 days for them to reply.
Furthermore, once you receive the Student Developer Pack on Github, we can say that these things are going to be the best benefits of the .edu email account: Youll get up to $110 in bonus AWS credits for a total sum of $75-$150, Bitnami Business 3 plan free for a whole year, DataDog Pro Account, including 10 servers.
This is free for 2 years, DigitalOcean $50 in platform credit for new users, Github unlimited private repositories while you are a student, Namecheap one-year SSL certificate and one-year domain name registration on the .me TLD .
So, lets commence our process of getting an Edu email for free without delaying.
How Might A Malicious Hacker Exploit An Expired Domain
Cybercrooks can use dropped domains for any attack vector that exploits an organizations identity, such as account takeovers or phishing campaigns that leverage false business invoices.
Criminal groups have even set up mail servers using expired domains. In turn, these can be used to gain access to social media accounts associated with the expired domain, or more worryingly, web services and SaaS applications.
There are many ways attackers can use old domains to their advantage, Tom McVey, solution architect at cloud security platform Menlo Security, told The Daily Swig.
For example, a manufacturing organisation could forget to renew their domain manufactory.com. Attackers could then purchase the domain and use it to host a website thats built to look just like the manufacturers site except every download link secretly contains infected files.
He adds: They could also execute phishing and social engineering attacks by emailing past clients with what looks to be a legitimate and safe email address, sales@manufactory.com.
The attackers essentially rely on the reputation of the domain to help increase the efficacy of their attacks.
Hijacked domains are used for identity-based attack vectors such as account takeovers or phishing campaigns
In a separate post, security expert Gabor Szathmari looks at how expired domains could be used to attack businesses in this case, law firms in Australia.
You May Like: Transfer Domain From Wix To Shopify