What Are The Key Ingredients For An Excellent Human Firewall
4.9/5Three Key Elements for Building an Effective Human Firewall
- Make People Care about Cybersecurity. A key element of building an effective human firewall is to make employees care about cybersecurity.
- Build Awareness and Knowledge.
Just so, what are the 3 key ingredients for an excellent human firewall?
- Business Continuity.
- US Healthcare Revenue Integrity.
- Vendor& Third-Party Risk.
Beside above, what 4 things are part of the cyber domain? divided cybersecurity into four domains: the physical domain the information domain the cognitive domain and the social domain (attention to ethics, social norms and a broad social
In respect to this, what describes a human firewall?
The definition of a human firewall is fairly straightforward. It is essentially a commitment of a group of employees to follow best practices to prevent as well as report any data breaches or suspicious activity. However, a human firewall can include Security Champions.
What things is part of cyber domain?
And domain is within the information environment consisting of the interdependent networks of information technology infrastructures and resident data, including the Internet, telecommunications networks, computer systems, and embedded pro- cessors and controllers.
The best firewalls for small businesses at a glance:Regardless of the content of the training, manager and employee training programs need at least the following basic elements to be successful.
The Future Is Zero Trust
Even as the world continues to change, the need for cybersecurity will remain a constant for businesses trying to protect their customers, employees, data, and IP. Cybercriminals thrive on chaos, agilely taking advantage during major disruptions to attack businesses that are defenseless. Worse, they also target enterprises that have a false sense of cybersecurity, believing their perimeters are protected and impenetrable. The most secure way forward for all business entities is to understand the limitations of traditional perimeter-based security and to step into the future by implementing the zero trust security model.
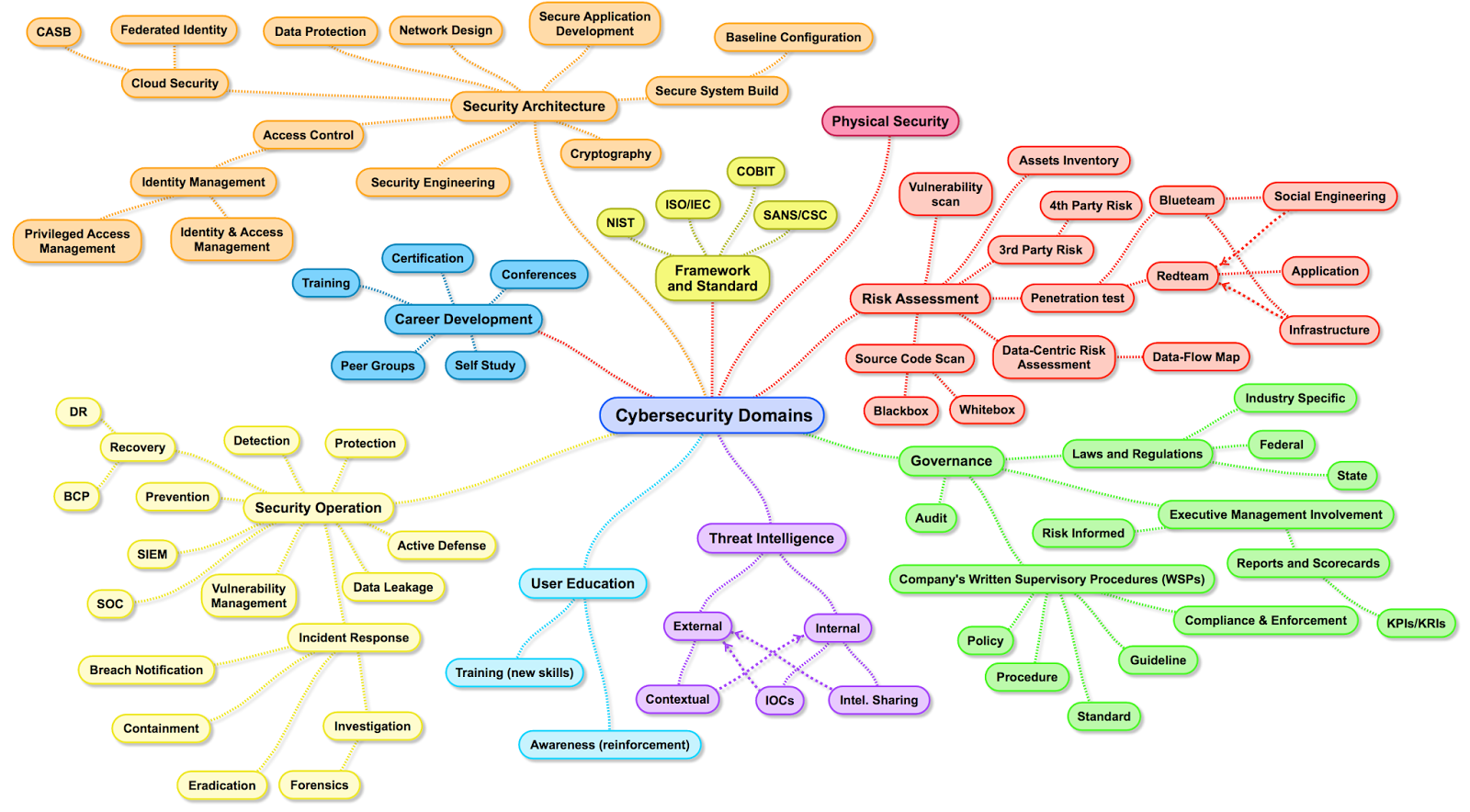
Quick Introduction Of 3 Domains Of Information Security
The 3 domains of information security are the following:
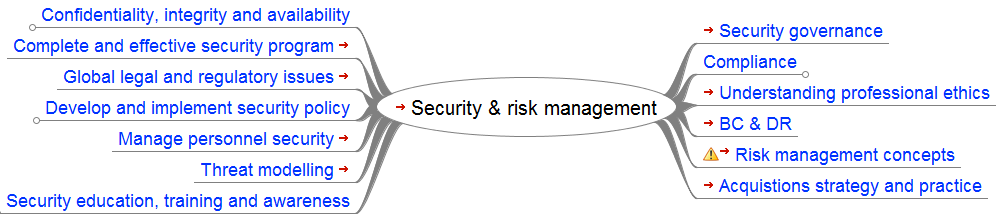
- Security and Risk Management
So what is information security means? It is preserving information and information systems.
So it helps to protect from the following:
Ads by IST
The terms of this following:
- Information security
Is generally used to exchange.
So these fields connect and share ordinary purposes.
Like protecting confidentiality. Also the integrity and availability of knowledge.
But, some details are different between them. But these difference lies.
- The subject approach
- The methodologies used
- The areas of concentration
So we can say that the main focus of information security. Is to protect the data of the confidentiality, integrity, and availability
That is it. Let us proceed to the three-domain of information security.
Read Also: How Much Are Domains
Where Do Cyber Attacks Come From
Cyber attacks are much more likely to occur through mundane errors like a user choosing an easy-to-guess password or not changing the default password on something like a router. Phishing is also a common way to gain access to a system, this involves extracting personal information under false pretences.
Creating A Security Domain
|
In the Create Security Domain dialog box, perform the following actions: In the Name field, type a name for the security domain. Set the Restricted Domain control toNo orYes. If the security domain is configured as a restricted domain , users who are assigned to this domain will not be able to see policies, profiles, or users configured in other security domains. |
Also Check: How Much Is It To Buy A Domain Name
What Do You Need To Know About Cyber Security
Cybersecurity is a practice that consists of technologies, processes, and controls that are designed to protect a network, system, and programs from cyber attacks. Having effective cybersecurity reduces the risk of cyber threats and also to troll the access of an authorized person to the network or system.
The Three Domains Of Application Security
It’s quite possible that this is not an original idea, but it’s something that occurred to me while we were discussing presentation planning for the year at the most recent OWASP NoVA chapter meeting. To me, application security can be neatly divided into three key domains: Architecture, Secure Coding, and Testing. Each of these domains represents a distinct set of practices that need to be addressed to have a truly complete appsec program.
What I find fairly interesting about these domains is that they’re not always all considered, whether it be in a software security program, or a Computer Science curriculum, or in contributions from key organizations like OWASP. In fact, it seems that Architecture, in particular, doesn’t get much love at all, while a nominal amount of time is spent on secure coding , and while the lion’s share of time is dedicate to the development of tools for testing.
ArchitectureWhen I say “architecture” here I’m really using the term loosely. In building construction, it is the job of architects to understand and define the requirements, and then translate them into a design that not only takes into consideration the customer’s vision, but that also makes sound decisions about structure, support, stability, and so on.
Tags:
Read Also: How Much For A Domain Name Per Year
Three Key Elements For Building An Effective Human Firewall
Cyber attacks arent just getting more frequent, they are also becoming significantly more vicious and sophisticated. According to the latest 2019 figures from the Ponemon Institutes Cost of Data Breach study, the average cost of a data breach has reached nearly $8.64 million in the US, alone. Yet todays cyber attacks have far-reaching negative impacts that continue to ripple outward long after the initial financial losses. These indirect damages include a tarnished brand reputation, lost relationships, and possible legal liability.
Cyber criminals count on the fact that busy people perform hundreds, if not thousands, of daily actions on a computer or device connected to the internet and they know that most of those actions are performed automatically and without much thought. As a result, the majority of todays data breaches result from human error, making cybersecurity a people problem as well as a technology issue.
The solution to this people problem goes beyond IT and involves cultivating an entirely new employee mindset around cybersecurity one that is motivated by more than facts and fear, one that is based on continually raising awareness and putting secure actions and decisions at the forefront of the company culture.
Security Professionals Are Expected To Be Proficient With A Range Of Security Techniques But Which Qualifications Do You Need To Progress Your Career
- Avinash W Kadam
Security professionals are expected to be proficient with a range of security techniques, but which qualifications do you need to progress your career?
Knowing which qualifications you need to progress your career is a dilemma faced by every information security professional. With a myriad of certificates to choose from, which one will help you prove that you can do your job better? Which one will be valued by employers?
A security professional has to be proficient with a range of security techniques. These include operating system security, network security, application security, penetration testing and incident management techniques.
Many suppliers offer certificates that are restricted to specific products. These are appropriate when IT security professionals need to be familiar with specific infrastructure or systems. But you should also consider acquiring certificates that are product independent. The Sans Institute, for example, offers some excellent certificates under the name global information assurance certification.
Organisations also look for business continuity management certification, and the Disaster Recovery Institute offers the CBCP certificate.
Security auditing is another qualification much sought-after by employers. Possessing a good understanding of security audit principles is a prerequisite to ensure that systems comply with audit requirements. Isaca offers the CISA for security auditors.
CV: AVINASH W KADAM
You May Like: Finding Out Who Owns A Domain
Domain : Security Operations
The Security Operations domain is where we monitor all of the tools we discussed in the Security Engineering domain. Most SOC positions are going to operate in this domain, as the name implies, but they need to have a good understanding of most of the other domains to be able to perform their job functions well. Some of the duties include:
- Threat hunting
- Threat Intel
- Forensics
I hope that helps clear up the different domains you may work with if you choose to enter cybersecurity. Bear in mind that in many organizations, cybersecurity professionals will work across multiple domains, but most will have one domain they focus on more than others.If we can help you in any way during this journey, please reach out via our Community Slack , or leave a comment below!
Zero Trust Architecture: The Complete Guide
Zero-Trust Architecture is an enterprises cybersecurity plan that utilizes zero-trust concepts and encompasses component relationships, workflow planning, and access policies. National Institute of Standards and Technology
Businesses are constantly under threat by bad actors looking for ways to penetrate security systems. Traditional perimeter defenses are increasingly ineffective in stopping the initial breach or preventing cyberattackers from then accessing the entire network, especially in the case of an insider threat. Thats where the zero trust security model comes into play, with its credo of trust nothing verify everything. This means that access to any resource within a network always must be subject to specified , or parameters. If these parameters are not met at any time, access is either denied or revoked. This model stands in complete contrast to traditional security models that assume implicit trust within the network perimeter, as with an employee who automatically has carte blanche within the entire network.
Read Also: Cost To Purchase A Domain Name
What Are The 10 Domains Of Cissp
Information Security Governance and Risk Management. Software Development Security.
A CBK sometimes simply called a Body of Knowledge refers to a peer-developed compendium of what a competent professional in their respective field must know, including the skills, techniques and practices that are routinely employed.
Beside this, What are four security domains give examples?
These include operating system security, network security, application security, penetration testing and incident management techniques. Many suppliers offer certificates that are restricted to specific products.
Likewise, What is an example of information security?
Examples of information security incidents include: Computer system intrusion. Unauthorized access to, or use of, systems, software, or data. Unauthorized changes to systems, software, or data. Loss or theft of equipment used to store or work with sensitive university data.
Also, What is the latest version of Cissp?
CISSP 2 Certified Information Systems Security Professional Official Study Guide, 8th Edition has been completely updated for the latest 2018 CISSP Body of Knowledge. This bestselling Sybex study guide covers 100% of all exam objectives.
How many Cissp are there in the world in 2019?
How Does Cyber Crime Affect Individuals
Cybercrime violates individuals privacy and the security of their data, particularly hacking, malware, identity theft, financial fraud, medical fraud, and certain offences against persons that involve the revealing of personal information, messages, images, and video and audio recordings without individuals consent
Don’t Miss: How Much Does It Cost To Buy A Domain
A Brief Overview Of The Eight Cissp Domains
² defines and organizes the CISSP domains based on its survey of the cybersecurity industry, often referred to as a job task study . The CISSP CBK domains are updated every three years to keep up ensure professionals are tested on the latest topic areas relevant to the roles and responsibilities of todays practicing information security professionals.
Many organizations rely on this test to ensure the readiness of their IT security teams. For example, the CISSP cert is DoD 8570 approved by the U.S. Department of Defense for workers conducting information assurance functions. Because CISSP is globally recognized and is one of the most sought-after certifications in information security, it is listed as one of the top security certifications you should acquire.
Here are the eight domains to be studied for the refreshed CISSP exam:
New Cissp Exam Version Effective May 1 2021
An updated version of the CISSP certification exam went into effect on May 1, 2021. The new version of the CISSP common body of knowledge reflects the most pertinent issues around cybersecurity, along with the measures for mitigating those problems.
The names and number of CISSP CBK domains are the same as in the 2018 CISSP exam, but the domain weights have changed for two of the eight domains. Essentially, domain four now has one percent less weight while domain eights weight has increased by one percent. The weights of all other domains remain unchanged. View the CISSP exam outline for even more detail about the ² CISSP CBK.
Recommended Reading: Transfer From Wix To Shopify
Stability Availability And Security
Availability is a major challenge in collaborative environments, as such environments must be stable and continually maintained. Such systems must also allow users to access required information with little waiting time. Redundant systems may be in place to offer a high level of fail-over. The concept of availability can also refer to the usability of a system.
Information security refers to the preservation of integrity and secrecy when information is stored or transmitted. Information security breaches occur when information is accessed by unauthorized individuals or parties. Breaches may be the result of the actions of hackers, intelligence agencies, criminals, competitors, employees or others. In addition, individuals who value and wish to preserve their privacy are interested in information security.
The CIA triad describes three crucial components of data and information protection which can be used as guides for establishing the security policies in an organization. Establishing and maintaining the organizations security policies can be a daunting task, but using the three-pillared strategic approach to cyber security can help you identify and manage cyber security risks in a methodic and comprehensive manner.
What Are The 5 Cybersecurity Domains
A NIST Security Framework is divided into five domains. In the NIST framework, there are five domains that are critical to creating a security plan that is holistic and successful. In addition to identifying, protecting, detecting, responding, and recovering, there is also restoring.
- Is Sharksurf Vpn As Fast?
- Is Sharing A Vpn With My Neighbor?
- Is Securelink A Vpn?
- What Is A Vpn That Takes Configurations Called?
- Is Secureline Vpn Worth It?
- Is Secureline Vpn Trustworthy?
- Is Secureline Vpn Torrent Friendly?
- How To Get Onion Over Vpn?
Don’t Miss: Transferring Domain From Wix To Shopify
What Is The Cia Triad
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
The three components of the CIA triad are discussed below: