Domain : Security Engineering
Security engineering usually refers to two key subdomains: network security and computer operations security. This domain is where your technical expertise is put to use in securing both the network and hosts from attacks. Its in this domain that we lump the following:
- Intrusion detection and prevention systems
- Host-based security tools
What Are The 3 Domains Of Information Security
A security domain is the list of objects a subject is allowed to access. More broadly defined, domains are groups of subjects and objects with similar security requirements. Confidential, Secret, and Top Secret are three security domains used by the U.S. Department of Defense , for example.
A security domain is a term used to conceptualize any grouping of computers, networks, or information technology infrastructure elements that fall under a specific security protocol. The domain is established as a restricted unit of those elements that then have a single authentication method for access to the elements within the security domain.
A Human Firewall Follows A Similar Concept Using Humans Your Workforce As The Barrier Between Cyber Criminals And Your Infrastructure
. First you must bring all the employees at your Company onboard with the ways to protect the Companys security system. Divided cybersecurity into four domains. Availability People Physical Integrity Confidentiality Cyber 2.
Beside above what 4 things are part of the cyber domain. Make it easy Dont overwhelm people with too much information at once. Select 4 Phishing emails Malicious links Clean Desk The Insider Badges Strong passwords Lost Thumb Drives webmail policies 3.
These attacks need a human to properly handle them in order to protect your company from loss. While building a human firewall a little education can go a long way. If employees dont care about a subject they won.
Malware The chance of downloading malware to your computer in the course of carrying out everyday work tasks is relatively high. The CIA Triad below outlines these three tenets. A human firewall is always aware of phone scams and is aware of which data to avoid sharing over the phone.
A security domain is the list of objects a subject is allowed to access. Which of these things is part of the CYBER domain. Ongoing training related to security threats and best practices to avoid falling for these threats.
It focuses on the understanding and alertness of employees and how they can make smarter security decisions. Ways to strengthen your Human Firewall 1. Confidential Secret and Top Secret are three security domains used by the US.
Human Firewall Tip 19 Zoom Cyber Security Challenges
Don’t Miss: What Is A Good Domain Name
Business Continuity And Disaster Recovery Planning
Plans must also be in place to preserve and continue business in the wake of a disaster or disruption of service. This domain emphasises two types of planning: business continuity planning and disaster recovery planning. Although the concepts are very similar in nature, there are some differences.
Business continuity planning is the process of making the plans that will ensure that critical business functions can withstand a variety of emergencies. In a healthcare environment, this includes how the necessary information to provide patient care is available. Disaster recovery planning involves making preparations for a disaster but also covers the procedures to be followed during and after a loss.8
There are four main phases in the business continuity planning process: 1) scope and plan initiation, 2) business impact analysis which, in healthcare, should include the impact to patient care, 3) business continuity plan development, and 4) plan approval and implementation.
Disaster recovery planning aids the organisation in making critical decisions and guiding action in the event of a disaster. For information security, the disaster recovery plan usually focuses on the data centres or computer rooms that house the servers and network equipment that comprise the information technology infrastructure. The plan details how these systems would be systematically recovered in the event of a disaster to the data centre or computer room.
Domains Of The Nist Security Framework
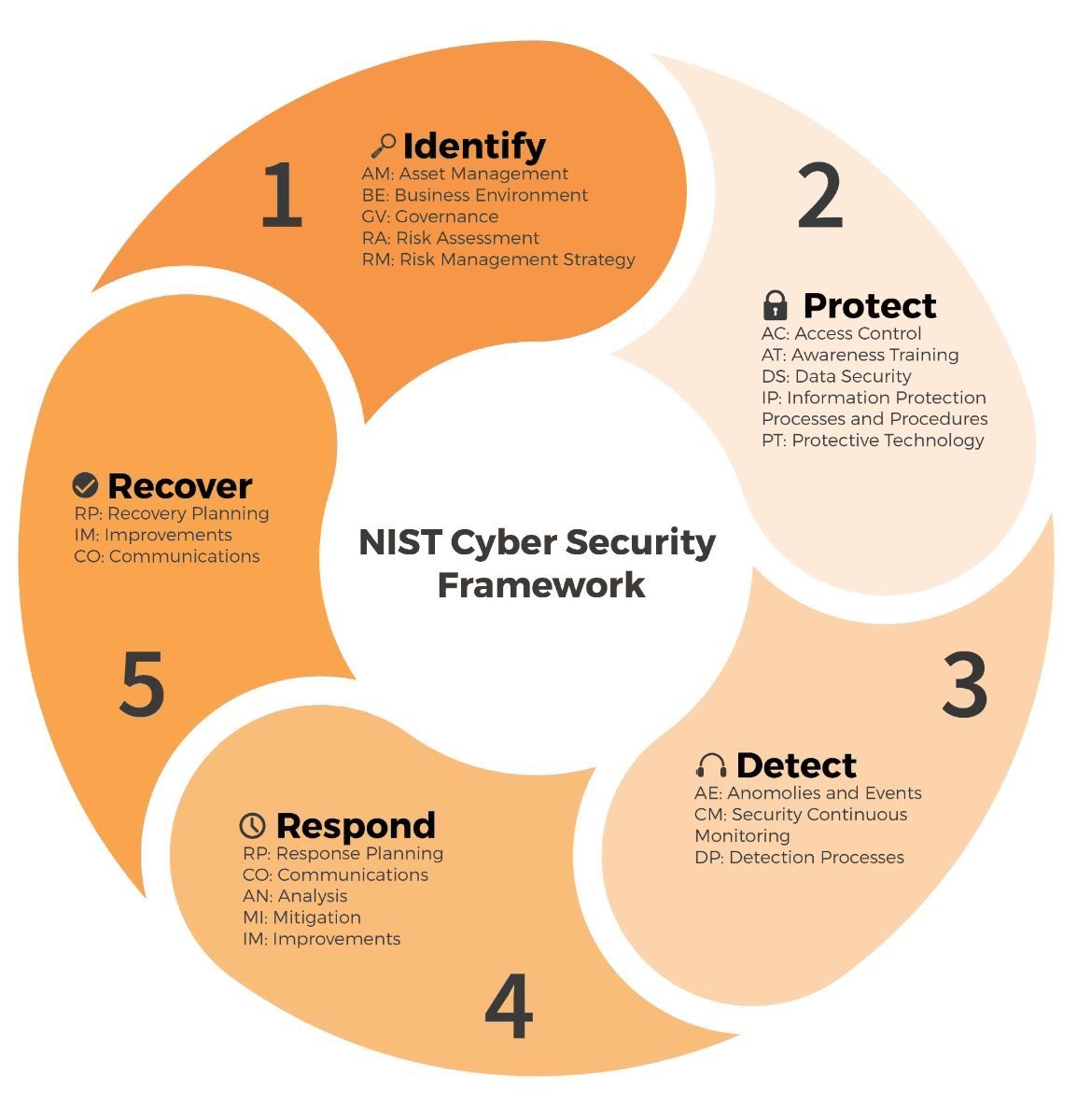
The five domains in the NIST framework are the pillars support the creation of a holistic and successful cybersecurity plan. They include identify, protect, detect, respond, and recover. These five NIST functions all work concurrently and continuously to form the foundation where other essential elements can be built for successful high-profile cybersecurity risk management.
Don’t Miss: How To Set Up Gmail With Your Own Domain
What Is Security Domain Under Cnssi 4009what Is Security Domain Under Cnssi 4009
NIST SP 800-53 Rev. 4 under Security Domain from CNSSI 4009. An environment or context that includes a set of system resources and a set of system entities that have the right to access the resources as defined by a common security policy, security model, or security architecture. See Security Domain.
The Third Pillar Is Data And Information Protection
This is the third and final article in a series addressing the three-pillar approach to cyber security. The first two pillars are people and process, The last pillar is data and information.
Data and information protection is the most technical and tangible of the three pillars. The data we gather comes from multiple sources, such as information technology , operational technology , personal data and operational data. It must be properly managed and protected every step of the way.
Read Also: How To Make Money With Domains
Principle : The Three Security Goals Are Confidentiality Integrity And Availability
All information security measures try to address at least one of three goals:
- Protect the confidentiality of data
- Preserve the integrity of data
- Promote the availability of data for authorized use
These goals form the confidentiality, integrity, availability triad, the basis of all security programs rel=nofollow> Figure 2.1). Information security professionals who create policies and procedures must consider each goal when creating a plan to protect a computer system.
The CIA triad.
FYI: CIA Triad
The principle of information security protection of confidentiality, integrity, and availability cannot be overemphasized: This is central to all studies and practices in IS. Youll often see the term CIA triad to illustrate the overall goals for IS throughout the research, guidance, and practices you encounter.
Dont Miss: What To Do After Buying A Domain
The Human Firewall Is A Crucial Element Of A Long
- Jessica Groopman,Kaleido Insights
Businesses must prioritize cybersecurity now more than ever. This process requires a broader scope than investing heavily in security technologies, however the tactic most companies have relied on to date. Relegating cybersecurity measures to IT-only mitigation overlooks the top cybersecurity risk: people.
Organizations have long deployed firewalls configurations of hardware and software that monitor and control network traffic based on predetermined security rules around their technical assets. Recently, cutting-edge AI-powered security applications came along as enhancements to the firewall concept. But, as sophisticated threats grow ever wider across distributed endpoints, targeting humans and their vulnerabilities, another kind of firewall is required: a human firewall.
Recommended Reading: Transfer Shopify Domain To Godaddy
Recommended Reading: How To Create Email With Own Domain In Gmail
Domain : Physical Security
A commonly overlooked domain, physical security refers to all the controls that should be applied to the physical hardware within our purview:
- Do we have fencing around our facility that forces individuals to enter and exit at the appropriately controlled point?
- Do we have security guards posted at every entrance to our organization?
- Are we securing the data center to only allow physical access to our servers to the authorized individuals?
- Do we have the proper HVAC system in place?
What Is A Ciso
Chief information security officers are people responsible for managing and ensuring the protection of an organizations information. This role may be a stand-alone position or be included under the responsibilities of the vice president of security or the chief security officer .
The responsibilities of a CISO include managing:
- Security operationsincludes real-time monitoring, analysis, and triage of threats.
- Cyber risk and cyber intelligenceincludes maintaining current knowledge of security threats and keeping executive and board teams informed of the potential impacts of risks.
- Data loss and fraud preventionincludes monitoring for and protecting against insider threats.
- Security architectureincludes applying security best practices to the acquisition, integration, and operation of hardware and software.
- Identity and access managementincludes ensuring proper use of authentication measures, authorization measures, and privilege granting.
- Program managementincludes ensuring proactive maintenance of hardware and software through audits and upgrades.
- Investigations and forensicsincludes collecting evidence, interacting with authorities, and ensuring that postmortems are performed.
- Governanceincludes verifying at all security operations operate smoothly and serving as a mediator between leadership and security operations.
Don’t Miss: How To Forward A Domain
Which Are The Three Main Security Pillars
When we talk about data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of three main components: confidentiality, integrity, and availability. On the same subject : What is cyber security developer?. Each component represents a fundamental objective of information security.
Description And Basic Aspects
The basic concept of the protocol is to tie the financial authorization process with online authentication. This additional security authentication is based on a three-domain model . The three domains are:
- Acquirer domain .
- Interoperability domain . It includes the Internet, merchant plug-in, access control server, and other software providers
The protocol uses XML messages sent over SSL connections with client authentication .
A transaction using Verified-by-Visa or SecureCode will initiate a redirection to the website of the card issuer to authorize the transaction. Each issuer could use any kind of authentication method but typically, a password tied to the card is entered when making online purchases. The Verified-by-Visa protocol recommends the card issuers verification page to load in an inline frame session. In this way, the card issuers systems can be held responsible for most security breaches. Today it is easy to send a one-time password as part of an SMS text message to users mobile phones and emails for authentication, at least during enrollment and for forgotten passwords.
The main difference between Visa and Mastercard implementations lies in the method to generate the UCAF : Mastercard uses AAV and Visa uses CAVV .
Dont Miss: How Much Do Domains Cost Per Year
Read Also: How To Make A Company Domain Email
Security Architecture And Engineering
Security Engineering comprises about 13% of the CISSP exam.
This domain covers several important information security concepts, including:
- Engineering processes using secure design principles
- Fundamental concepts of security models
- Security capabilities of information systems
- Assessing and mitigating vulnerabilities in systems
- Cryptography and
- Designing and implementing physical security.
Identity And Access Management
Identity and Access Management comprises about 13% of the CISSP exam.
This domain helps information security professionals understand how to control the way users can access data. It covers:
- Physical and logical access to assets
- Identification and authentication
- Integrating identity as a service and third-party identity services
- The identity and access provisioning lifecycle.
Read Also: How To Set Up Gmail With Godaddy Domain
What Are The Four Pillars Of Security Strategy
Contents
The four pillars are zero trust architecture, supply chain security, the cybersecurity framework of the National Institute of Standards and Technology, and certifications. On the same subject : What are the 3 types of software security?.
- Zero-Trust architecture improves government security.
- A secure supply chain is more vital than ever.
What are the 4 pillars of security? There are four basic principles that apply to most security systems: authentication, authorization, confidentiality, and integrity.
Three Key Elements For Building An Effective Human
. Architecture Secure Coding and Testing. Malicious Links Webmail Policies Strong Passwords. In this article we take a look at the 14 security domains specific to ISO 27001.
Each of these domains represents a distinct set of practices that need to. Empower Your Organizations Defenders by Putting the Right Tools in the Right Hands. The CISM credential focuses on four domains.
Security and risk management is one of the largest domains in cybersecurity. The security architecture domain refer to a plan and set of principles that describe the security services that a system is required to provide to meet the needs of its users the. Ad Compare Best Computer Security Software 2022.
As the name implies this security domain covers the legal issues associated with computer. Confidential Secret and Top Secret are three security domains used by the US. Information security governance information security risk management and compliance information security program development and.
A security domain is considered. A network with a different security domain is kept separate from other networks. Which of these things is part of the cyber domain.
Confidential Secret and Top Secret are three security domains used by the US. Protect Your PC From Viruses Online Threats. Department of Defense DoD for example.
Physical People and Cyber. Confidential Secret and Top Secret are three security domains used by the US. Stay Safe Online Today.
2 To build a culture of security.
Read Also: How To Give Your Website A Domain Name
What Are The 5 Cybersecurity Domains
A NIST Security Framework is divided into five domains. In the NIST framework, there are five domains that are critical to creating a security plan that is holistic and successful. In addition to identifying, protecting, detecting, responding, and recovering, there is also restoring.
- Is Sharksurf Vpn As Fast?
- Is Sharing A Vpn With My Neighbor?
- Is Securelink A Vpn?
Dont Miss: Transferring Domain From Wix To Shopify
What Are The Goals Of Information Security
The ultimate goal of information security is to maintain the CIA triad within an organization. The elements of the CIA triad are:
Confidentiality: This means ensuring that only the authorized users have access to information. Whenever a company suffers from a data breach or data leak and individuals information is accessed by criminals, the public or employees that dont have the proper authorization, confidentiality has been compromised. Some of the key security controls that you can use to maintain confidentiality are:
Many companies like KFC and coca cola keep their intellectual property and trade secrets in secure vaults.
Notice how the hash changes significantly just because of a period at the end.
Availability: To ensure that the information is accessible to authorized people whenever it is needed. An example of this would be a website like Netflix. For most companies they want availability of at least 99.99%, which means that 99.99% of the time you go to Netflix you should be able to access the services that you want. In order to do this there are several practices you can implement to ensure that your company will have a high uptime:
This an example of redundancy from Amazon Web Services resiliency recommendations
Digital Signatures Explained
Also Check: How To Connect Domain To Email
How To Achieve 360 Cybersecurity Approach By Covering These Three Domains Ie People Processes And Technology
Security threats are constantly evolving and your security measures need to adjust accordingly. You should have strong mechanism to protect your ogragnization with help of People, Process & Technology.
There should be a comprehensive framework to help you & evaluate your current cybersecurity landscape and ensure you have proper protection.
360° Cybersecurity approach : This Approach covers the three main domains of people, process and technology & these three steps-
Step 1 is to identify and assess your current level of threat, risks and protection.
Identify> Threat-> Risk -> Strategy -> Security review.
Step 2 is to take corrective action where gaps are identified.
Protect > People -> Process -> Technology.
Step 3 is to monitor the system, respond to threats and incidents and allow you to report to your board and regulators
Monitor> Real Time -> Scheduled-> Unscheduled -> Security Review.
You May Like: Vistaprint Domain Transfer
From Information Security Domain What Is The ‘social Engineering’
A non-technical method of intrusion which hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter.
The threat of technology-based security attacks is well understood, and IT organizations have tools and processes
in place to manage this risk to sensitive corporate data. However, social engineering attacks are more challenging to
manage since they depend on human behavior and involve taking advantage of vulnerable employees. Businesses
today must utilize a combination of technology solutions and user awareness to help protect corporate information.
Financial gains are the primary motivation of social engineering. Social engineering attacks are costly especially in large organizations. New employees are most susceptible to social engineering technique.
Hope this helps.
In simplest form the social engineering is a method to manipulate the enduser and to test the behavior of the enduser to extract valuable information.
Don’t Miss: What Is A Domain Name Used For
Security Professionals Are Expected To Be Proficient With A Range Of Security Techniques But Which Qualifications Do You Need To Progress Your Career
- Avinash W Kadam
Security professionals are expected to be proficient with a range of security techniques, but which qualifications do you need to progress your career?
Knowing which qualifications you need to progress your career is a dilemma faced by every information security professional. With a myriad of certificates to choose from, which one will help you prove that you can do your job better? Which one will be valued by employers?
A security professional has to be proficient with a range of security techniques. These include operating system security, network security, application security, penetration testing and incident management techniques.
Many suppliers offer certificates that are restricted to specific products. These are appropriate when IT security professionals need to be familiar with specific infrastructure or systems. But you should also consider acquiring certificates that are product independent. The Sans Institute, for example, offers some excellent certificates under the name global information assurance certification.
Organisations also look for business continuity management certification, and the Disaster Recovery Institute offers the CBCP certificate.
Security auditing is another qualification much sought-after by employers. Possessing a good understanding of security audit principles is a prerequisite to ensure that systems comply with audit requirements. Isaca offers the CISA for security auditors.
CV: AVINASH W KADAM